
Moving assets across blockchains is a superpower in the multi-chain era. Maybe you want lower fees on Arbitrum, a new DeFi opportunity on Base, or an NFT mint on Polygon. The fastest way there is usually a cross-chain bridge. Yet bridges remain one of the most targeted parts of Web3. Poorly implemented contracts, centralized controls, thin liquidity, and phishing sites have cost users billions.
This guide is your preflight checklist for cross-chain bridge safety. It is designed for beginners and pros who want a dependable process for safe cross-chain transactions. We included a compact set of blockchain bridge safety tips and a practical template for crypto bridge security checks that you can reuse for every route.
By the end, you will know how to verify a bridge, how to run a small test, how to confirm token types, and how to avoid the mistakes that lead to losses.
Introduction to Blockchain Technology and Cross Chain
Blockchain technology has transformed digital finance by introducing decentralized, transparent, and tamper-resistant systems for recording transactions. However, as the blockchain ecosystem has grown, so has the number of independent blockchain networks, each with its own protocols, assets, and smart contract environments. This fragmentation creates barriers for users and developers who want to move assets or data between different blockchain networks.
Cross chain bridges have emerged as a powerful solution to this challenge. By connecting otherwise isolated blockchains, cross chain bridges enable seamless asset transfers, smart contract interactions, and data sharing across multiple blockchain ecosystems. These bridges play a crucial role in unlocking the full potential of blockchain technology, allowing users to move tokens, interact with decentralized applications, and access liquidity on different blockchain networks. As a result, cross chain bridges are foundational to the vision of a truly interconnected, interoperable blockchain world.
Why Bridge Safety Matters
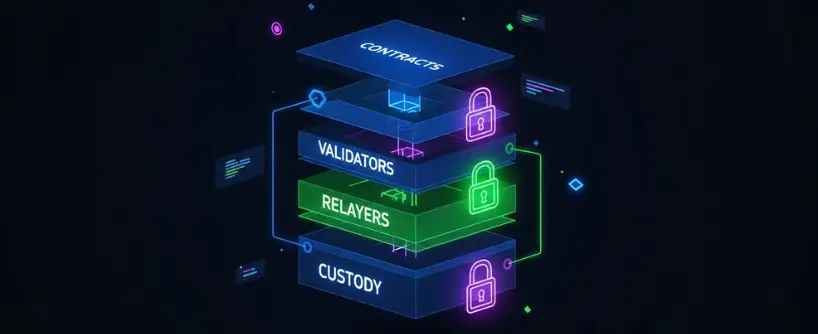
Cross-chain bridges connect networks that cannot natively communicate. To do that, they rely on smart contracts, validator sets, relayers, and sometimes custodians. The bridge protocol is the set of rules and smart contracts that facilitate asset and data transfers between blockchains, and its design is fundamental to bridge safety. These components must coordinate correctly. If a code flaw exists in the bridge protocol, a validator set is compromised, or a wrapped asset loses backing, funds can be lost. Because bridges aggregate value, they are high-value targets for attackers. The complexity of bridge protocols increases the attack surface, making them more susceptible to exploits if not properly secured.
You do not need to be a security researcher to protect yourself. You need a disciplined process. The five checks below are the highest-leverage steps you can take to reduce cross-chain bridge risks while keeping your workflow fast.
Bridge Infrastructure and Designs
What Are Bridge Infrastructures?
Bridge infrastructures are the technical backbone that allows cross chain bridges to operate smoothly and securely. At their core, these infrastructures are made up of smart contracts, oracles, validators, and communication protocols that work together to facilitate cross chain transactions. Smart contracts automate the locking, minting, and releasing of assets, while oracles and validators monitor events and verify cross chain messages. Communication protocols ensure that information flows reliably between different blockchains, even when they use different coding languages or consensus mechanisms.
The strength of a bridge’s infrastructure directly impacts its ability to withstand attack vectors and maintain the integrity of cross chain transactions. Secure cross chain bridges are built on robust infrastructures that have been thoroughly tested and audited, minimizing the risk of exploits and ensuring that users’ assets are protected throughout the bridging process.
Bridge Designs and Their Importance
The design of a cross chain bridge is a critical factor in its security and usability. Bridge designs can range from trusted models, which rely on centralized entities to manage asset transfers, to trustless models that use smart contracts and decentralized algorithms to automate the process. Each approach comes with its own set of trade-offs: trusted bridges may offer speed and simplicity but introduce single points of failure, while trustless bridges can enhance security but may be more complex and slower.
Choosing the right bridge design is essential for managing security risks. Poorly designed bridges can expose users to threats such as private key compromise, where attackers gain access to the keys controlling bridge contracts, or smart contract vulnerabilities that allow funds to be drained. As bridges operate across multiple blockchains, any weakness in their design can have far-reaching consequences. That’s why it’s important to understand how different bridge designs handle private keys, smart contract logic, and overall risk before using them for cross chain transactions.
The Top 5 Safety Checks Before Bridging
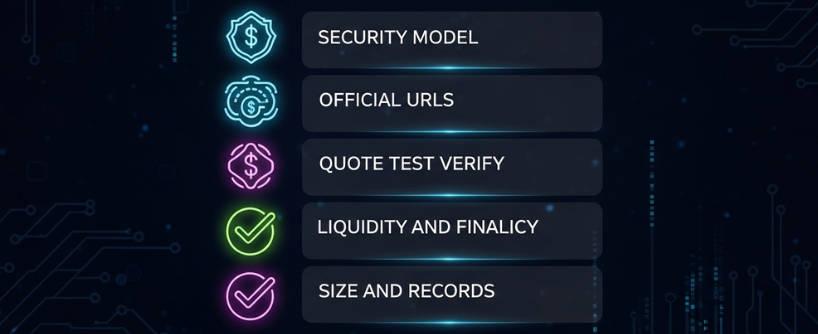
Confirm the Security Model and Reputation
What to do: Identify which model the bridge uses and whether it has a strong track record.
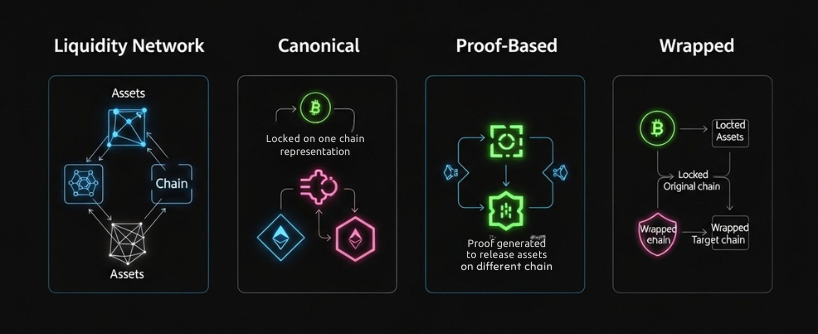
- Liquidity network: Pools of native assets on each chain with off-chain relayers or validators that watch deposits and trigger releases. Fast and convenient, but you must trust operational controls and pool management. Understanding the security vulnerabilities associated with each model is crucial for informed decision-making.
- Canonical bridge: The official network bridge that locks on the source chain and mints a canonical representation on the destination. Security aligns with the chain’s own design, but withdrawals can be slow.
- Proof-based bridge: Uses light clients and on-chain verification of proofs. Strong trust properties, more complex, sometimes higher gas cost.
- Wrapped or synthetic asset bridge: Locks originals with a custodian and mints wrapped tokens. Flexible, but introduces custody and depeg risk.
How to check reputation:
- Look for recent audits from well-known firms, not just logos. Read the executive summary and unresolved issues section.
- Search for bug bounties. A funded bounty invites white-hat scrutiny. Participation in a bug bounty program is a proactive cross chain security measure, allowing external security researchers to identify vulnerabilities before attackers do.
- Review incident history. Has the team paused the bridge before? How did they compensate users?
- Scan community reports. Consistent positive user feedback, clear documentation, and responsive support are good signs.
Why it matters: Choosing a model that fits your risk tolerance is the core of cross-chain bridge safety. For high-value transfers, you may prefer a canonical or proof-based route even if it takes longer. For routine convenience, a strong liquidity network can be acceptable with small, split transfers. Robust cross chain security practices, such as regular audits and bug bounty programs, are essential for minimizing security vulnerabilities in bridge protocols.
Use Only Official URLs and Contract Addresses
What to do: Open the bridge from official documentation or verified social links. Bookmark it. Before you approve or send, confirm that the contract address in your wallet matches the address listed in the docs or a reputable explorer page.
Practical steps:
- Type the URL manually or navigate from the project’s documentation repository.
- Check the SSL certificate and spelling. Phishing sites often use near-identical domains.
- In your wallet, click the contract address of the token or the approval target and open it on the block explorer. Compare it to the address published by the project.
- If a site asks for token approvals to unknown contracts, stop.
Why it matters: Many bridge losses have nothing to do with sophisticated exploits. Users approved malicious contracts or used imitation sites. This single check dramatically cuts your risk and sits at the top of any real crypto bridge security checks list.
Quote, Test, Verify: The Three-Step Transaction Routine
A predictable routine is your best defense. Before you bridge size, always run Quote, Test, Verify.
A. Quote: Enter your route and amount. Review the entire quote:
- Expected output amount
- Bridge fee and any trading fee
- Estimated time to finality
- Whether a destination claim transaction is required
- Slippage tolerance settings if a swap is involved
If the UI does not show these clearly, choose a different bridge. Lack of transparency is a red flag in safe cross-chain transactions.
B. Test: Send a small amount, enough to be meaningful but not painful if lost. Confirm that:
- The source transaction finalized
- The destination address received funds
- The time and fee matched the quote within reason
C. Verify: Open the destination token in your wallet and click through to the contract on the explorer. Confirm the contract address is the official token your target apps use. On some routes you can receive a wrapped variant with the same ticker. You need to know what you received before you interact with DeFi. Receiving native tokens on the destination chain, instead of wrapped tokens, can reduce your exposure to cross-chain vulnerabilities and complexities.
Why it matters: The Quote, Test, Verify routine eliminates the most common user errors and validates a route before you commit. It is the fastest way to avoid bridge hacks that rely on phishing or incorrect token types.
Check Liquidity Depth, Route Health, and Finality
What to do: Before sending, check whether the destination pool has sufficient liquidity, whether the route is experiencing delays, and how long finality is expected to take.
How:
- Many bridges display pool inventory, utilization, or a simple status indicator. Liquidity providers play a crucial role in maintaining sufficient pool inventory and enabling smooth asset transfers across chains.
- Look for a status page or a Twitter account that reports incidents or high load.
- Read the fine print on finality, especially for canonical bridges that use challenge windows.
- Keep native gas on both chains. If a destination claim transaction is required, you need gas to finish.
Why it matters: Liquidity networks can temporarily run out of inventory on one side when flows are one-way. Proof-based and canonical bridges may require multiple confirmations. Knowing this in advance saves you from unnecessary panic and helps you schedule transfers.
Size, Split, and Save Records
What to do: Treat each transfer as a position with risk. Limit size, split big moves into smaller batches, and save every hash.
Practical tips:
- Set a maximum transfer size that you could tolerate losing in a worst-case event.
- Split large amounts into several smaller transfers across time or routes. This often improves pricing in shallow pools.
- Save the source and destination transaction hashes, the quoted minimum output, and a screenshot of the confirmation page.
- Use a simple tracking sheet for treasury moves so you always know where funds live.
Why it matters: Bridges compress several moving parts. If a surprise occurs, having smaller batches and organized records helps support teams help you and keeps your own accounting clean.
Chain Bridge and Communication Protocols
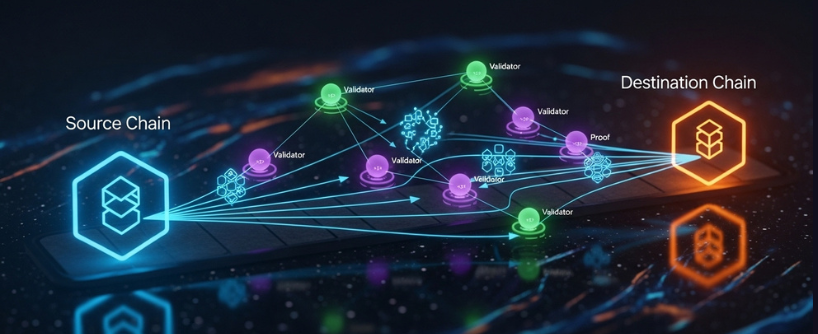
Chain bridges rely on sophisticated communication protocols to enable cross chain transactions between different blockchain networks. These protocols are responsible for securely transmitting information such as transaction proofs, asset ownership, and cross chain messages between the source chain and the destination chain. Depending on the bridge, communication protocols can be centralized, relying on a single operator, or decentralized, distributing trust among multiple validators or relayers. Decentralized protocols are generally considered more secure, as they reduce the risk of a single point of failure.
Real-world examples highlight the importance of robust communication protocols. The Ronin Bridge, for instance, uses a decentralized protocol to facilitate transactions between Ethereum and the Ronin sidechain, while Binance Smart Chain employs its own protocol to support seamless asset transfers across different blockchain networks. These protocols are essential for ensuring that assets are transferred accurately and efficiently, without exposing users to unnecessary risks.
However, the complexity of cross chain bridges makes them an attractive target for hackers. High-profile bridge exploits, such as the Poly Network hack, have resulted in significant losses and underscored the need for strong security measures. Attackers often exploit vulnerabilities in bridge designs, smart contracts, or communication protocols to drain funds from bridge contracts. To counter these threats, secure bridge designs incorporate advanced security measures such as hardware security modules, formal verification of smart contract code, and regular security audits. Bug bounty programs also play a key role in identifying and addressing potential vulnerabilities before they can be exploited.
By prioritizing secure communication protocols and investing in robust bridge infrastructure, the blockchain community can reduce the risk of cross chain bridge exploits and protect the integrity of the entire ecosystem. This commitment to security is essential for building trust and enabling the continued growth of cross chain asset transfers and blockchain interoperability.
Cross-Chain Bridge Risks Explained in Plain Language
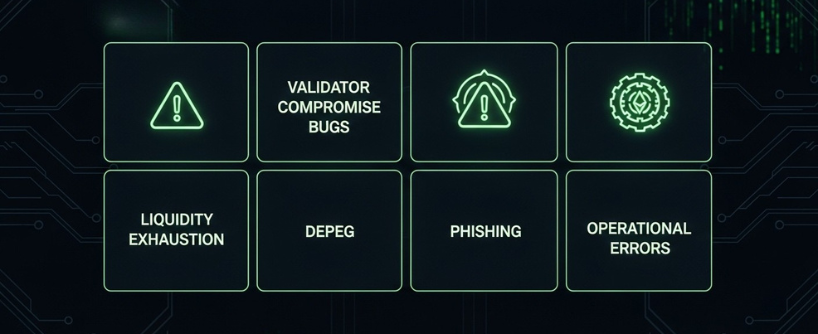
A checklist only works if you understand what it is protecting against. Here are the core cross-chain bridge risks and how the checks above address them. Cross-chain bridges face several attack vectors, including smart contract vulnerabilities, validator compromises, and network-layer exploits.
Smart contract bugs
- Vulnerabilities in locking, minting, accounting, or swap logic can drain funds. Logic flaws and logic errors in smart contract code can lead to critical vulnerabilities; static analysis and fuzz testing are essential for identifying these issues before deployment.
- Mitigation: Choose audited bridges, read incident history, and avoid brand-new code for large transfers.
Validator or relayer compromise
- A small committee could sign an invalid message that releases funds to an attacker. Private key compromises and poor private key management are common causes of such exploits.
- Mitigation: Favor proof-based or canonical bridges for size. If you use a liquidity network, research validator diversity and slashing design.
Liquidity exhaustion
- One-way traffic can empty destination pools, causing long delays or poor prices.
- Mitigation: Check route health and pool inventory. Split transfers or change direction if needed.
Wrapped asset depeg
- Custodians who hold original tokens can be hacked or lose keys, breaking the link to wrapped tokens.
- Mitigation: Prefer native assets on both sides when possible. If you must use wrapped tokens, understand redemption mechanics and custody.
Phishing and fake UIs
- Imitation sites trick users into approving malicious contracts.
- Mitigation: Only use official URLs and verify contract addresses. Bookmark trusted links.
Operational errors
- Wrong address, wrong network, wrong token.
- Mitigation: The Quote, Test, Verify routine and keeping gas on both chains prevent most mistakes.
In addition, implementing alert systems can help detect suspicious activity and respond to threats in real time.
Step-by-Step Example: Bridging USDC from Ethereum to Arbitrum
Use this hands-on walkthrough as a template for safe cross-chain transactions.
Preparation
- Wallet connected to Ethereum.
- Sufficient ETH for gas.
- Arbitrum network added to your wallet with a small amount of ETH for destination gas.
Open the official bridge URL
- Navigate from the project’s documentation. Bookmark the link.
Review the quote
- Enter route and amount.
- Check expected output, fees, and time estimate.
- Confirm if a destination claim is required.
Approve tokens
- Approve only the amount you plan to send, not an unlimited approval when possible.
Send a small test
- Execute a small transfer. Wait for delivery.
- Confirm that the Arbitrum address received USDC.
Verify token contract
- Click the token in your wallet and open the contract in the explorer.
- Compare to the official USDC contract on Arbitrum.
Send the full transfer
- If the test checks out, repeat for the larger amount.
- Save source and destination hashes.
Post-transfer review
- Check balances, note the final received amount, and update your tracking sheet.
This flow is quick once you practice it a few times and fits neatly into real crypto bridge security checks.
Blockchain Bridge Safety Tips You Can Apply Today
- Bookmark official bridge URLs and their status pages.
- Keep a buffer of native gas on every network you touch.
- Turn on wallet phishing protection and set custom RPCs from trusted providers.
- Approve only what you need and revoke stale approvals periodically.
- Use a hardware wallet for signing, especially for approvals.
- Avoid bridging during major network incidents or when volatility is extreme.
- For teams, enforce a policy that requires a small test first and that records hashes in a shared log.
These simple blockchain bridge safety tips cover 80 percent of day-to-day protection and help you avoid bridge hacks born of haste or confusion.
Frequently Asked Questions
What is the safest type of bridge for large transfers?
For high-value moves, many users prefer canonical bridges or proof-based bridges because their trust model aligns with the network or relies on on-chain verification of proofs. These bridges are considered the safest for transferring assets or conducting asset transfers between blockchains. Cross-chain bridges, in particular, enable users to transfer assets across multiple chains, increasing flexibility and access to different blockchain ecosystems. They can be slower and sometimes more expensive, but they reduce dependency on external validator committees. For routine small transfers, a reputable liquidity network may be acceptable when you follow the safety checks.
How do I recognize a phishing site that imitates a bridge?
Phishing sites often copy the front end perfectly but change the destination contracts. Always navigate from official docs, verify the domain spelling, and compare the approval or bridge contract address in your wallet to the address listed in the documentation or explorer. If anything looks different, stop and recheck. This single habit prevents many losses.
Why do some routes require a claim transaction on the destination chain?
Certain bridges deliver a voucher or message that you must claim, which lets you choose the destination address and finalize the transfer. This can improve flexibility or security, but it requires gas on the destination chain. Keep a small amount of the destination chain’s native token to avoid getting stuck.
My transfer is taking longer than the quote. What should I do?
First, check the bridge’s status page or Twitter for incident notices. Then inspect pool inventory if the bridge shows it. For canonical bridges, verify whether a challenge window is in progress. If there is no incident and your test transfer worked earlier, patience is often the answer. If hours pass without updates, open a support ticket with both transaction hashes and your screenshots.
How can I reduce the chance of receiving the wrong token on the destination chain?
After the test transfer, click the token in your wallet and open the contract address in the explorer. Compare it to the token address used by your target application or the one listed in reputable docs. If the bridge supports both native and wrapped versions, the UI should state which version you will receive. When in doubt, transfer a tiny amount and check compatibility with the app you intend to use.
What is the advantage of splitting large transfers into smaller batches?
Splitting reduces the impact of any single failure and can also improve pricing when pools are shallow. If a pool’s depth is limited, a very large single transfer might incur higher slippage or queue until liquidity is refilled. Multiple smaller transfers also create more granular records that are easier to reconcile.
Do I need audits and bug bounties if I only send small amounts?
Yes, but apply proportional caution. Audits and bug bounties give confidence that independent experts reviewed the code and that the team welcomes scrutiny. For small amounts, the routine of Quote, Test, Verify and official URLs might be enough, yet audits remain a strong signal.
Can I bridge without revealing my transaction to the public mempool?
Some bridges and relays accept private transactions that route directly to block producers, which can reduce the risk of MEV interception on the source chain. This is helpful when bridging during volatile markets or when a swap is part of the route. Check the bridge’s documentation for private RPC options.
Are wrapped tokens always risky?
Wrapped tokens are not inherently unsafe. Risk depends on custody, mint and burn controls, and transparency. If the custodian is compromised or redemption halts, the wrapped token can depeg. If you hold significant amounts of a wrapped token, understand how redemption works and what guarantees support it.
What records should I keep for accounting or support?
Save the source and destination transaction hashes, the address you sent from and to, the quoted minimum output, the time of submission, and a screenshot of the confirmation screen. If you use a corporate wallet or DAO treasury, store these in a shared folder and update a simple log. These records speed up support and make tax reporting easier.
Glossary
Blockchain bridges: Protocols or infrastructure that connect two or more blockchain networks, enabling the transfer of assets and data between them. Blockchain bridges are critical for interoperability but are also frequent targets for exploits due to their complexity and the value they secure.
Blockchain network: The underlying distributed infrastructure that consists of nodes, consensus mechanisms, and protocols, enabling the operation and interaction of a blockchain. Blockchain networks are foundational for cross-chain interactions and must be secured to prevent exploits across multiple chains.
Blockchain projects: Initiatives or organizations that develop, maintain, or contribute to blockchain technology, often collaborating to establish interoperability standards, enhance security, and ensure regulatory compliance across the ecosystem.
Blockchain platforms: Comprehensive frameworks or environments that support the development and deployment of decentralized applications (dApps) and smart contracts. Blockchain platforms often implement security practices like Zero Trust Architecture and enable interoperability through cross-chain bridges.
Cross chain infrastructure: The set of protocols, tools, and security mechanisms that facilitate secure and reliable communication, asset transfers, and data exchange across multiple blockchain networks. Robust cross chain infrastructure requires thorough audits, formal verification, and comprehensive testing.
Infrastructure providers: Entities or organizations that supply the foundational technology and services for blockchain networks, including nodes, APIs, and security solutions. Infrastructure providers play a key role in standardizing protocols, collaborating with regulators, and securing cross-chain communication.
One blockchain: Refers to a single, individual blockchain network, as opposed to solutions that operate across multiple blockchains. Many interoperability protocols are designed to work beyond just one blockchain, enabling cross-chain functionality.
BNB Chain: A prominent blockchain network known for its high throughput and DeFi activity. The BNB Chain bridge exploit is a notable security incident where attackers stole a significant amount of assets by exploiting vulnerabilities in the bridge.
Bridges account: Specialized accounts or smart contracts used by blockchain bridges to hold and manage assets during cross-chain transactions. Bridges accounts are high-value targets for hackers due to their central role in asset custody and the technical complexity involved in securing them.
Cross-chain bridge: Infrastructure that moves tokens between blockchains by locking and releasing, minting and burning, or routing through liquidity pools.
Canonical bridge: The official bridge supported by a blockchain or rollup team.
Proof-based bridge: A system that verifies cryptographic proofs from one chain on another using light clients.
Liquidity network: A bridge model that releases funds from a destination pool and rebalances inventory later.
Wrapped token: A token on one chain that represents an asset locked on another chain.
Finality: The point at which a transaction is effectively irreversible on a blockchain.
Relayer or validator set: Off-chain agents or committees that observe events and submit messages to destination chains.
Slippage: The difference between the quoted and executed output due to price or inventory changes.
Depeg: Loss of parity between a wrapped token and the original asset it represents.
Status page: A public page where a project reports outages, degraded performance, or maintenance.
A Compact Checklist: Crypto Bridge Security Checks
Use this on every transfer:
- Open the bridge from official documentation and bookmark it.
- Confirm the security model and read recent audits or bounties.
- Enter your route to view the quote. Review fees, output, and time.
- Approve only what you need, not unlimited, if the UI allows.
- Send a small test transfer. Wait for delivery.
- Verify the destination token contract in the explorer.
- Send the main transfer. Keep gas on both chains.
- Save hashes, screenshots, and notes in your log.
- If size is large, split into batches or consider a more conservative route.
- Revoke stale approvals periodically and keep your bookmarks clean.
This ten-step routine takes a few minutes and enables safe cross-chain transactions with confidence.
Conclusion
Bridges unlock the multi-chain world, but they demand respect. The best way to practice cross-chain bridge safety is not to memorize every exploit. It is to build a habit:
- Choose reputable bridges with clear security models and current audits.
- Use only official URLs and correct contract addresses.
- Run the Quote, Test, Verify routine.
- Check route health and keep gas on both sides.
- Size and split transfers, then save your records.
Follow these blockchain bridge safety tips and your cross-chain workflow will feel calm and predictable. You will move capital where it is most productive, interact with new ecosystems, and do it with a process that helps you avoid bridge hacks rather than hoping they never happen.
About Bitunix
Bitunix is one of the world’s fastest growing professional derivatives exchanges, trusted by over 3 million users across more than one hundred countries. Ranked among the top exchanges on major data aggregators, Bitunix processes billions in daily volume and offers a comprehensive suite of products including perpetual futures with high leverage, spot markets, and copy trading. Users can trade bitcoin and other major cryptocurrencies on the platform, taking advantage of advanced trading features. Known for its Ultra K line trading experience and responsive support, Bitunix provides a secure, transparent, and rewarding environment for both professional and everyday traders. Bitunix Academy adds structured lessons so you can build skills while you trade.
Bitunix Global Accounts
X | Telegram Announcements | Telegram Global | CoinMarketCap | Instagram | Facebook | LinkedIn | Reddit | Medium
Disclaimer: Trading digital assets involves risk and may result in the loss of capital. Always do your own research. Terms, conditions, and regional restrictions may apply.









