
Moving value between blockchains is no longer optional. Users lend on one chain, trade on another, and hold NFTs or stablecoins on a third. That reality creates a single recurring task for almost everyone in crypto: bridging. The problem is that not all bridges look the same or carry the same risks. Some rely on a centralized operator with fast settlement and familiar customer support. Others use trust minimized verification and accept slower exits as trade for stronger assurances. A growing set of systems land in the middle and try to capture the best features of both worlds.
This guide gives you a clear, practical comparison of centralized vs decentralized vs hybrid bridges. You will learn how each design moves assets, what you must trust, the common failure modes, and how to choose a route that fits your transfer size, urgency, and risk tolerance.
[ez-toc]
Centralized vs Decentralized Bridges: Why They Matter in a Multi Chain World
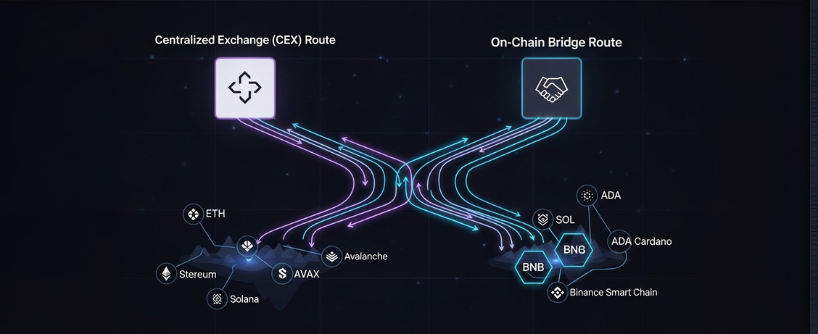
Ethereum offers the broadest DeFi and NFT ecosystem. Layer 2 networks such as Arbitrum, Optimism, Base, and zkSync reduce fees and increase throughput. Alternative layer 1s and smart chains like BNB Chain (also known as Binance Smart Chain), Avalanche, and Solana attract users with specific applications and cost profiles. Builders choose the venue that fits their product. Users follow the opportunity. Blockchain technology underpins this multi-chain future, enabling cross chain interoperability and connecting blockchain ecosystems. That flow of capital creates constant demand for cross chain transfers.
Asset transfers, token transfers, and transferring assets between chains are essential for users and developers in a multi-chain future, allowing seamless participation across blockchain ecosystems.
You can move funds in two general ways:
- Send assets to a centralized exchange, trade internally, then withdraw to another chain. This works but introduces custody, withdrawal queues, and account based controls.
- Use a bridge, which is an on chain or partly on chain system that transfers value from chain A to chain B.
Bridges power arbitrage, liquidity deployment, payroll, treasury moves, and basic user onboarding. Picking the right bridge keeps costs low, reduces delays, and most importantly protects your assets from unnecessary risk.
Introduction to Blockchain Interoperability
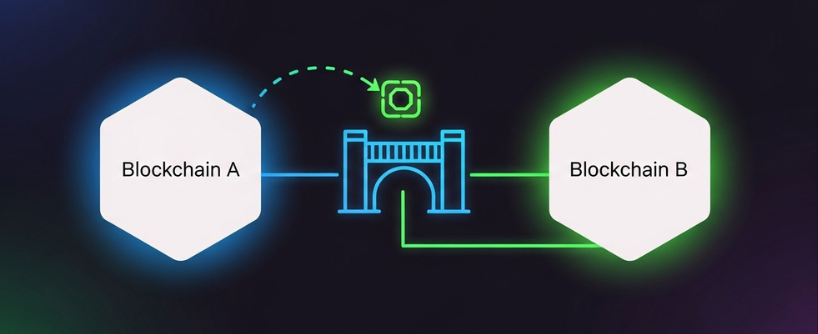
Blockchain interoperability is the foundation that allows different blockchain networks to communicate, interact, and share value seamlessly. In a world where multiple chains like Ethereum, BNB Chain, Avalanche, and others, each offer unique features and communities, the ability to transfer assets and data across these networks is essential for a thriving blockchain ecosystem. This interoperability unlocks new opportunities for users and developers, enabling access to a broader range of decentralized applications, services, and liquidity.
At the heart of blockchain interoperability are cross chain bridges, also known as blockchain bridges. These protocols connect two or more blockchain networks, making it possible to transfer assets, such as tokens or coins, from a source chain to a destination chain. By bridging different blockchain networks, users can move digital assets, participate in DeFi protocols, and interact with dApps across multiple chains without being locked into a single ecosystem.
The Three Main Bridge Types in Blockchain
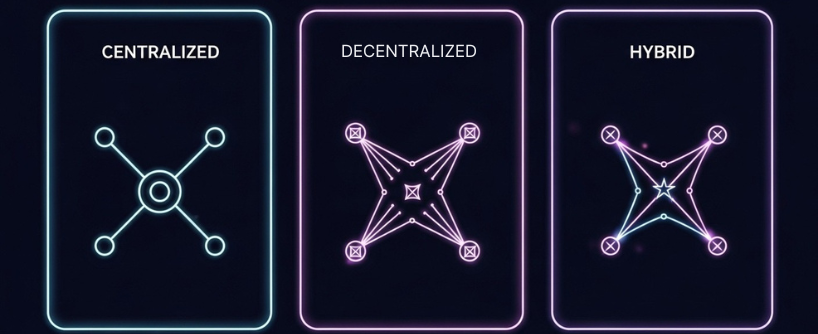
Most production systems fall into one or more of these categories. The bridge architecture of these systems determines their security, scalability, and interoperability, and there are several types of blockchain bridges, including federated bridges, custodial bridges, and trustless bridges, each with distinct roles in DeFi and cross-chain asset movement:
- Centralized bridges: A single operator or a tight multisig controls the vault that holds source chain assets and the mint or release on the destination. These are also known as custodial bridges, as they are managed by a central authority or bridge operator who is responsible for asset custody, minting wrapped tokens, and managing associated security risks. They often support many long tail tokens and provide fast, simple UX. Trusted bridges fall into this category, offering speed and ease of use but requiring trust in the operator.
- Decentralized bridges: Trust minimized systems verify cross chain messages on chain. These are also referred to as trustless bridges, as they operate without a central authority, relying on smart contracts, cryptography, and consensus algorithms to ensure security and transparency. Two common patterns are proof based bridges that run a light client for the other chain, and canonical bridges that are part of a rollup or appchain’s core stack. They aim for cryptographic security rather than trusting an external signer.
- Hybrid blockchain bridges: These combine a decentralized protocol for routing and accounting with service operators that provide liquidity and submit messages. Some hybrids use federated bridges, where a trusted group of validators manages asset transfers, and liquidity pools to facilitate fast and secure cross-chain transfers. Most liquidity network bridges fit here. They release funds from destination pools first, then rebalance inventory later. Hybrids aim to deliver speed without abandoning responsible controls. Liquidity pools, funded by users or market makers, play a crucial role in enabling seamless asset transfers and earning rewards in these systems.
Each type can be excellent in the right context. The key is understanding what you must trust and the trade you accept in return for convenience.
How Bridges Move Assets
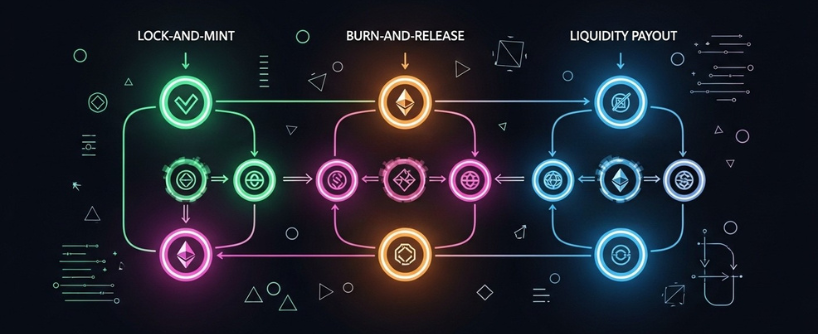
At a high level, users encounter three movement patterns, all typically enabled and secured by smart contracts that handle asset transfer and verification:
- Lock and mint: Tokens are locked in a smart contract or custodian on the source chain, a process known as locking assets. These locked assets remain immobilized until the user returns. A representation is then minted on the target chain, allowing users to utilize the asset there. Returning home burns the representation and releases the original.
- Burn and release: If the asset already exists natively on both chains, the protocol burns on the source and releases from reserves on the destination. This is common for canonical token transfers and connections between a layer 2 and its parent layer 1.
- Liquidity payout: The protocol pays the user out of an existing liquidity pool on the destination chain as soon as it sees proof of the source deposit. Liquidity pools and liquidity pool mechanisms facilitate transferring assets and token transfers across chains by providing immediate access to funds. Later, the protocol rebalances inventory through on chain trades or off chain netting.
The final user experience depends on the verification method that connects the two chains. Let us look at that in detail for each bridge style.
Centralized Bridges
How they work
A centralized bridge uses a custodian that controls the source chain vault and the mint or release logic on the destination. The custodian may be a regulated company, an exchange, or a smart contract with keys held by a small group using a multisig. Users deposit on chain A to an address managed by the custodian. After enough confirmations arrive, the custodian credits or releases the requested asset on chain B.
What you are trusting
- The custodian will not lose keys or run away with funds.
- The custodian will honor withdrawals even during market stress.
- The custodian’s internal accounting and security are robust.
- If the bridge issues wrapped assets, those tokens are always redeemable one for one.
Pros
- Speed and simplicity: Centralized operators can release funds quickly, often within minutes, because they do not need to verify complex proofs on chain.
- Broad token support: It is straightforward to list many assets, even those with non standard formats.
- Customer support: If a deposit memo is wrong or a transaction needs investigation, a centralized desk can help.
- Predictable UX: Many users are familiar with this approach from exchanges.
Cons
- Centralized bridge risks: A single point of failure creates custodial risk. History shows that key compromise or insider failure can cause total loss.
- Bridge exploits: Notable bridge exploits and hacks have resulted in major financial losses, often due to vulnerabilities in centralized bridges.
- Wrapped asset exposure: If the issuer has problems, the wrapped token may trade at a discount.
- Regulatory and blacklist risk: Withdrawals can be delayed or denied for compliance reasons.
- Opaque reserves: Unless audited, you rely on the operator’s claims about solvency.
When a centralized bridge makes sense
- Small transfers where speed matters more than trust minimization.
- Funding a trading account on a chain that is otherwise hard to reach.
- Assets that have no supported decentralized route.
When using a centralized route, reduce risk by limiting per transfer size, verifying official addresses, and keeping position time short. If you receive a wrapped token, check its redemption path and market acceptance before relying on it.
Decentralized Bridges
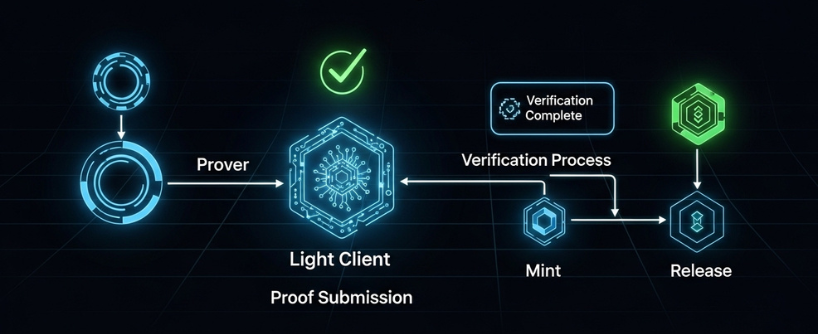
Decentralized bridges attempt to remove human trust from the message path. Trustless bridges use smart contracts to enable secure transfers and cross chain transactions, allowing assets and data to move between blockchains without relying on centralized authorities.
In proof-based verification, the bridge uses cryptographic proofs to verify that an event occurred on the source chain. Cross chain messaging is a key feature of decentralized bridges, enabling not only asset transfers but also generalized data and smart contract interactions between blockchains. This approach allows for composability and trustless interoperability.
Proof based or light client verification
A contract on chain B runs a light client for chain A. The bridge sends block headers and Merkle proofs from chain A. The verification contract on chain B checks that the source event truly occurred in a finalized block and then allows the corresponding release or mint. No external validator needs to vouch for the message.
Pros
- Strong security model. You rely on the cryptography and consensus of the two chains, not a third party.
- No custody of pooled funds by a company. Assets are controlled by code, not by a single operator.
- Composability. Other contracts can reason about proofs on chain.
Cons
- Cost and complexity. Verifying consensus and proofs on chain is expensive, especially across heterogeneous chains.
- Limited routes. Many pairs do not have compatible clients or practical proof systems yet.
- Longer finality. The system may wait for more confirmations, which increases settlement time.
Canonical or native bridges
Rollups and appchains often provide an official bridge that is part of their core protocol. For example, optimistic rollups submit checkpoints to Ethereum and support a challenge period to contest fraud. Withdrawals back to layer 1 are delayed until the relevant checkpoint finalizes.
Pros
- Aligned incentives. The team that secures the network maintains the bridge.
- Predictable redemption. You burn the representation on the rollup and receive the native asset on L1 after the proof window.
- No trusted multisig. The design follows the chain’s consensus.
Cons
- Slow exits. Fraud proof windows or finality periods can take days.
- Limited asset set. Canonical bridges focus on native tokens and common standards.
- UX friction. Some users find the wait and claim steps confusing.
Decentralized bridge advantages summarized
- Low reliance on any single operator.
- Clear, verifiable rules on chain.
- Stronger resilience against censorship and key loss.
- Suited for large treasury moves where assurance matters more than speed.
Hybrid Blockchain Bridges
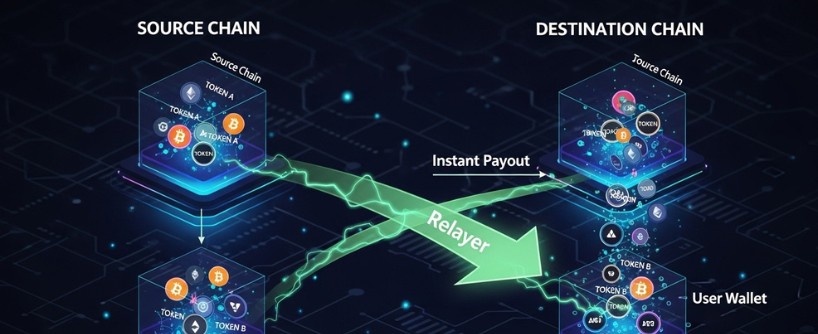
Many widely used routes are hybrids. They blend decentralized accounting with off chain service roles to achieve fast settlement while keeping trust assumptions bounded and visible.
Hybrid bridges may incorporate federated bridges and unified liquidity pools to support a wide range of supported routes, enabling robust cross chain infrastructure for a multi chain future. This approach helps connect DeFi and traditional financial systems, reduces liquidity fragmentation, and improves transaction efficiency across multiple blockchains.
Liquidity network bridges
LPs deposit funds into liquidity pools on multiple chains. These liquidity pools act as banks, enabling the protocol to facilitate transfers and asset transfers across different blockchains quickly and securely. When you send USDC from Ethereum to Arbitrum, the system releases USDC from the Arbitrum liquidity pool to your wallet as soon as it observes your Ethereum deposit. Later the protocol rebalances inventory by encouraging LPs to move funds the other way or by executing trades. Validators or relayers watch both chains and submit messages. Most systems include economic security such as bonded operators and slashing for misbehavior. Synapse Protocol is a notable example of a bridge that uses liquidity pools to facilitate cross-chain asset transfers across supported networks.
Pros
- Fast delivery: Payouts arrive in a few minutes because they come from existing inventory.
- Native asset delivery: Many routes deliver native tokens rather than wrapped versions.
- Good UX: Clear quotes, guaranteed minimums, and auto routing across multiple pools.
Cons
- Inventory risk: One sided flow can deplete destination pools, leading to queues or worse pricing.
- Operator trust: You must trust validators or relayers to run honestly and keep keys safe.
- Pricing complexity: Quotes depend on pool utilization, gas on both chains, and rebalancing costs.
Hybrid design outside of liquidity networks
Some bridges use a decentralized protocol to approve messages but rely on whitelisted sequencers for ordering or batching. Others accept proof based verification for large settlements and use an optimistic fast path for small retail transfers, with backstops and insurance funds. The space is evolving quickly, and many hybrids are transparent about their risk model so users can choose.
Cross Chain Bridge Comparison Criteria
Evaluating bridge types in blockchain is easier when you apply a consistent set of criteria. The key features of each bridge type, such as enhanced security, the ability to handle high value transfers, and supported networks, are important comparison points when assessing which protocol best fits your needs.
Security model
- Who or what must be trusted to release funds
- Are there stakes, slashing, or proofs on chain
- How big is the validator set or multisig quorum
- Maintaining security is critical, especially as intent-based architectures and new blockchain solutions aim to simplify user experience without compromising safety.
Finality and exit time
- How long until funds arrive
- Are there challenge windows or checkpoints
- Do you need to manually claim on the destination chain
Asset quality
- Native tokens vs wrapped representations
- Redemption guarantees for synthetics
- Market acceptance of the delivered token
Liquidity depth and capacity
- TVL on each route
- Utilization during peak hours
- Fees or throttles when pools are imbalanced
Transparency and governance
- Public audits and bug bounties
- Timelocks for upgrades
- Open documentation for incidents and parameters
Costs
- On chain gas on both sides
- Protocol fees and relayer fees
- Slippage or inventory spread
User experience
- Quote clarity and guaranteed minimum outputs
- Error handling and customer support
- Clear indication of which asset you will receive
Selection criteria
- The choice of bridge depends on your specific use case and risk tolerance, as different protocols offer varying levels of security, speed, and asset support.
Use these criteria to run a cross chain bridge comparison before sending large amounts, especially for high value transfers.
Security Models and Failure Modes
Security is the deciding factor for many treasuries. Crosschain bridges face significant security risks, as demonstrated by numerous bridge hacks and bridge exploits in the past. Notable incidents, such as the Ronin Bridge hack, have exposed vulnerabilities in smart contracts and custodial frameworks, resulting in substantial financial losses and highlighting the need for robust security measures. Here is what can go wrong and how each bridge type mitigates the risk.
In response to these threats, leading protocols have adopted enhanced security measures, such as intent-based architecture and protocol-level intent verification, to reduce user errors and strengthen overall safety.
Centralized failure modes
- Key compromise or insider abuse: A single admin or a small multisig can drain funds.
- Operational outage: Withdrawals pause during stress or upgrades.
- Wrapped asset depegging: If reserves are impaired, the token trades below parity.
Mitigations include multi region HSM secured keys, external audits of reserves, real time proof of liabilities, and clear legal accountability. Users can mitigate by limiting exposure time and amount.
Decentralized failure modes
- Smart contract bugs: A logic error in proof verification or minting can be exploited.
- Consensus or reorg risk: If the source chain reorgs after a proof is accepted, an invalid message could pass.
- Economic attacks: If a small committee is used for emergency operations, it may collude.
Mitigations include formal verification, multiple independent audits, large bug bounties, and waiting for deep finality. For rollups, the challenge window exists precisely to catch fraud.
Hybrid failure modes
- Validator or relayer collusion: A committee signs an invalid message.
- Liquidity exhaustion: Pools run dry in one direction and quotes degrade or halt.
- Oracle or pricing manipulation: Poor inputs cause bad quotes or unintended payouts.
Mitigations include bond and slashing, public validator sets, diversified operators, inventory incentives that rebalance quickly, and transparent health dashboards. Well run hybrids publish incident reports and improve controls over time.
Realistic Costs and Time to Finality
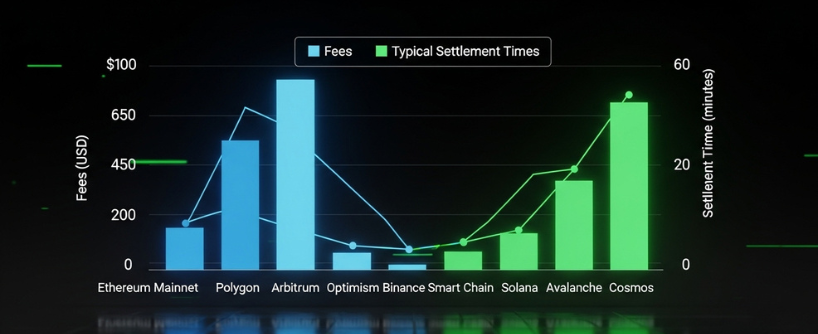
Costs vary by chain congestion and route design. Here is what you can expect:
- Centralized bridges often charge a flat or percentage fee and pay destination gas themselves. Delivery is typically minutes.
- Proof based decentralized bridges charge mainly gas for verification and may require a claim transaction on the destination. Delivery ranges from minutes to hours. Canonical rollup exits back to L1 take longer due to the challenge period.
- Liquidity network bridges present a single quote that includes protocol fee, relayer fee, and a spread that reflects pool utilization. Delivery is usually a few minutes, but can slow when one side is depleted.
- Some multichain bridges, such as Avalanche Bridge, are designed for blockchain interoperability and offer instant finality for token transfers, enabling fast and secure cross-chain transactions.
When comparing, include all components: source gas, destination gas if needed, protocol fees, and slippage. A seemingly cheaper route can cost more after you account for a claim transaction or a poor fill.
Case Studies and Illustrative Scenarios
Scenario 1: Personal transfer, 500 dollars stablecoins to a layer 2
- Priority: convenience and speed
- Best fit: a reputable liquidity network bridge or the canonical on ramp if it offers instant credits
- Why: inventory payout is fast, quotes are clear, and the amount is small enough that added trust is acceptable
Scenario 2: DAO treasury, 2 million dollars from L2 back to Ethereum
- Priority: assurance over speed
- Best fit: canonical bridge with posted checkpoints and published audits
- Why: fraud proof windows and on chain verification reduce reliance on external parties. The DAO can plan around timing.
Scenario 3: Arbitrageur moving ETH from chain A to B in minutes
- Priority: settlement time
- Best fit: hybrid liquidity network with deep pools and guaranteed minimum outputs
- Why: a few minutes of edge in a market strategy matters more than the slight additional trust
Scenario 4: New token with only wrapped versions on destination chains
- Priority: token availability
- Best fit: centralized or hybrid bridge that lists the token
- Caveat: verify redemption path and monitor peg health. Use smaller tranches until liquidity is proven.
How to Choose a Bridge in Practice
Use this decision flow before every significant transfer.
- Define the transfer goal: Amount, urgency, and the exact asset you want to receive.
- List available routes: Include canonical, proof based, centralized, and hybrid options.
- Check security posture: Look for recent audits, public validator sets, and timelocks.
- Assess liquidity and time: Read route health dashboards. Avoid routes with depleted destination pools.
- Compare total cost: Include on chain gas, protocol fees, and slippage.
- Verify destination asset: Native token is preferred. If wrapped, confirm redemption and market acceptance.
- Send a test: For large amounts, send a small transfer to validate UX and timing.
- Record details: Keep transaction hashes, quotes, and timestamps for accounting and for support if you need it.
Compliance and Policy Considerations
Institutions must consider additional factors when comparing bridge types:
- KYC or blacklist behavior: Centralized bridges may require identity checks or block sanctioned addresses.
- Accounting treatment: Wrapped tokens may be booked differently from native assets.
- Jurisdiction: A custodian’s legal location can matter for recourse.
- Audit trails: Proof based systems provide clean on chain evidence. Liquidity networks should publish logs that link source and destination events.
A written bridge policy that maps size thresholds to acceptable routes helps teams stay consistent. For example, a policy might require canonical or proof based designs for transfers above a certain dollar value.
Best Practices for Safer Bridging
- Use official links and verified contracts. Bookmark them to reduce phishing risk.
- Keep destination gas: Hold a small balance of the native token on the destination so you can interact immediately.
- Set realistic slippage: Too loose invites poor fills. Too tight can cause failures during volatile periods.
- Avoid novel routes during incidents: When a major chain is congested or undergoing upgrades, wait for green status.
- Split big transfers: Multiple smaller moves reduce the risk of a single failure and can secure better pricing.
- Watch approvals: Approve only what is needed and revoke unused allowances periodically.
- Monitor pool health in real time: Many hybrid bridges show pool depth and utilization.
- Document your process: Keep a runbook for team members that lists preferred routes and fallback options.
Cross Chain Bridge Comparison Table
| Criterion | Centralized bridge | Decentralized bridge | Hybrid liquidity network |
| Primary trust | Custodian or small multisig | Cryptographic proofs or canonical protocol | Validator or relayer set plus economic security |
| Typical speed | Minutes | Minutes to hours, L2 to L1 can be days | Minutes, sometimes near instant |
| Asset type | Often wrapped or custodied | Native or canonical representation | Usually native on both sides |
| Token coverage | Broad, includes long tail | Narrower, focused on standard assets | Moderate to broad |
| Failure modes | Key loss, insolvency, blacklists | Contract bugs, reorg edge cases | Validator collusion, pool exhaustion |
| Transparency | Varies by operator | High, on chain proofs | Medium to high, public dashboards and slashing preferred |
| Best use | Small urgent transfers, uncommon tokens | Large treasuries, high assurance moves | Fast retail transfers and active strategies |
Frequently Asked Questions
What is the safest bridge type for large transfers?
For most organizations, the safest default is a decentralized bridge that relies on on chain verification, especially the canonical bridge of a rollup or appchain. It may take longer, but it reduces human trust and custody risk.
Why do some routes deliver wrapped tokens while others deliver native assets?
Lock and mint designs need a representation on the destination, which is a wrapped asset. Liquidity networks usually fund destination payouts with the native asset already there. Canonical bridges often handle native assets in both directions. If you receive a wrapped token, verify its redemption path and adoption.
What is a hybrid bridge in plain language?
A hybrid bridge blends a decentralized protocol with off chain service roles. The protocol sets rules and tracks balances. Validators or relayers observe deposits and help release funds from destination pools. The goal is speed with visible, bounded trust.
How can I reduce the risk of a bridge failure?
Split large transfers, prefer routes with audits and public validator sets, watch pool utilization, set conservative slippage, and keep destination gas ready. For very large amounts, prefer proof based or canonical paths.
Why do hybrid bridges sometimes quote worse during volatile markets?
Inventory is a scarce resource. When most users move in one direction, the destination pool can deplete. To attract rebalancing or deter further drain, the protocol widens spreads or limits size. That shows up as a worse quote.
Are centralized bridges always bad?
No. They can be convenient and reliable for small, fast transfers. The risk arises when users keep large balances exposed to a single custodian or rely on thinly documented wrapped assets.
How do I check that a bridge is real and not a phishing copy?
Use links from official documentation or reputable aggregators, verify contract addresses on block explorers, and confirm that the UI warns about approvals and shows the exact asset you will receive. Bookmark trusted URLs.
Do I need to claim funds on the destination chain?
Some routes auto deliver. Others require a claim transaction that you must sign after the message is verified. Check the instructions before you send, and be sure you hold a bit of the destination chain’s gas token.
What is the difference between a router and a bridge?
A router selects a path among bridges and DEXs and presents a single quote. The bridge is the underlying mechanism that actually moves value. Good routers disclose which bridge they use and the associated risks.
Can I use insured bridges?
A few protocols and third party services provide coverage for specific failure modes, for example validator collusion. Read exclusions carefully. Insurance can complement but not replace careful route selection.
What is the portal token bridge?
The portal token bridge is a cross-chain solution powered by Wormhole. It enables seamless asset transfers across multiple blockchain networks, supporting a wide range of platforms and using a decentralized validation system to secure transactions.
What is the wormhole bridge and has it had security issues?
The wormhole bridge is a cross-chain bridge that connects different blockchain networks, such as Ethereum and Solana, to facilitate asset transfers between them. Notably, it experienced a major security exploit resulting in a $320 million loss due to a smart contract flaw.
What are bidirectional bridges?
Bidirectional bridges enable two-way token transfers and asset synchronization between blockchain networks. They support complex cross-chain functionalities, such as DeFi, NFTs, and multi-chain dApps, by allowing seamless interaction and movement of assets in both directions.
Glossary
- Bridge: Software and contracts that move value or messages between blockchains.
- Bidirectional bridges: Cross-chain bridges that enable two-way token transfers and asset synchronization between different blockchain networks, supporting complex functionalities such as DeFi, NFTs, and multi-chain dApps.
- Portal token bridge: A cross-chain solution powered by Wormhole that enables seamless asset transfers across multiple blockchain networks, supporting numerous platforms and utilizing a decentralized validation system.
- Wormhole bridge: A cross-chain bridge connecting blockchain networks like Ethereum and Solana, facilitating asset transfers between chains. It is notable for its role in major security incidents, such as the $320 million exploit due to a smart contract flaw.
- Federated bridges: Blockchain interoperability solutions managed by a trusted group of validators, balancing trust, speed, and reliability for efficient and secure asset transfers between multiple blockchains, commonly used in DeFi, NFTs, and cross-chain asset movement.
- Custodial bridges: Cross-chain bridges managed by a central authority or entity, offering user-friendliness and regulatory compliance but introducing security risks and requiring users to trust the operator.
- Trustless bridges: Decentralized asset transfer mechanisms that operate without a central authority, relying on smart contracts, cryptography, and consensus algorithms to ensure secure and transparent cross-chain transactions.
- Bridge operator: A trusted third party or entity responsible for managing asset transfers in trusted or custodial bridge systems, controlling deposits, minting wrapped tokens, and managing associated security risks.
- Unified liquidity pools: Liquidity pools used in multichain bridges, such as Stargate, to enable seamless and instant token transfers across different blockchains, reducing fragmentation and improving transaction finality.
- Canonical bridge: The official bridge operated or endorsed by a network, often used for native assets.
- Light client: A contract that verifies block headers and proofs from another chain to enable trust minimized messaging.
- Liquidity network bridge: A system that pays users from destination pools first and rebalances later.
- Wrapped asset: A token that represents an asset locked elsewhere. It depends on the custodian or issuer for redemption.
- Finality: The point at which a transaction is practically irreversible on a blockchain.
- Checkpoint: A periodic state summary submitted from one chain to another to help finalize withdrawals.
- Relayer or validator: An operator that observes deposits and submits cross chain messages.
- Utilization: Share of a pool’s inventory that is in use. High utilization can slow or halt transfers.
- Timelock: A delay between proposing and executing privileged actions, giving users time to react.
- Slashing: Economic penalty for misbehavior by a validator or bonded operator.
- MEV: Maximal Extractable Value. Profit extracted by reordering or inserting transactions; can affect fees and slippage.
- Router: An interface or contract that chooses paths across bridges and exchanges to deliver the quoted amount.
Conclusion
There is no single best bridge for every transfer. Centralized bridges trade speed and wide asset support for custodial risk. Decentralized bridges trade convenience for stronger, on chain assurances. Hybrid blockchain bridges try to balance both by paying from destination liquidity and enforcing operator behavior with bonds, slashing, and transparency.
If you remember only three things, make them these:
- Match the bridge type to your goal. Use trust minimized paths for size and speed focused paths for small daily moves.
- Evaluate security, finality, asset quality, liquidity, and cost as a set. A weakness in any one can dominate the outcome.
- Send a test transfer, keep good records, and monitor route health. Good process is your best protection.
With a clear understanding of centralized vs decentralized vs hybrid bridges, you can move confidently through the multi chain world and keep your capital working where it is most effective.
About Bitunix
Bitunix is a global cryptocurrency derivatives exchange trusted by over 3 million users across more than 100 countries. At Bitunix, we are committed to providing a transparent, compliant, and secure trading environment for every user. Our platform features a fast registration process and a user-friendly verification system supported by mandatory KYC to ensure safety and compliance. With global standards of protection through Proof of Reserves (POR) and the Bitunix Care Fund, we prioritize user trust and fund security. The K-Line Ultra chart system delivers a seamless trading experience for both beginners and advanced traders, while leverage of up to 125x and deep liquidity make Bitunix one of the most dynamic platforms in the market.
Bitunix Global Accounts
X | Telegram Announcements | Telegram Global | CoinMarketCap | Instagram | Facebook | LinkedIn | Reddit | Medium
Disclaimer: Trading digital assets involves risk and may result in the loss of capital. Always do your own research. Terms, conditions, and regional restrictions may apply.

