
Earning yield in crypto does not have to mean chasing the highest number on a dashboard. A professional approach treats yield as a byproduct of providing a useful service to the network, measured against clear risk controls. Staking pays you for securing a chain. Conservative DeFi pays you for lending liquid, high quality collateral or for providing liquidity to well designed markets. The objective is simple. Preserve principal, earn steady returns, and avoid tail events that erase months of progress.
This guide lays out a full framework for staking and conservative DeFi. You will learn how yield is created, how to evaluate validators and staking providers, how to classify DeFi risks, how to set position limits, and how to monitor everything with a short runbook that anyone on your team can follow. The tone is practical, the checklists are specific, and the examples focus on responsible sizing rather than speculation.
What Is Yield In Crypto
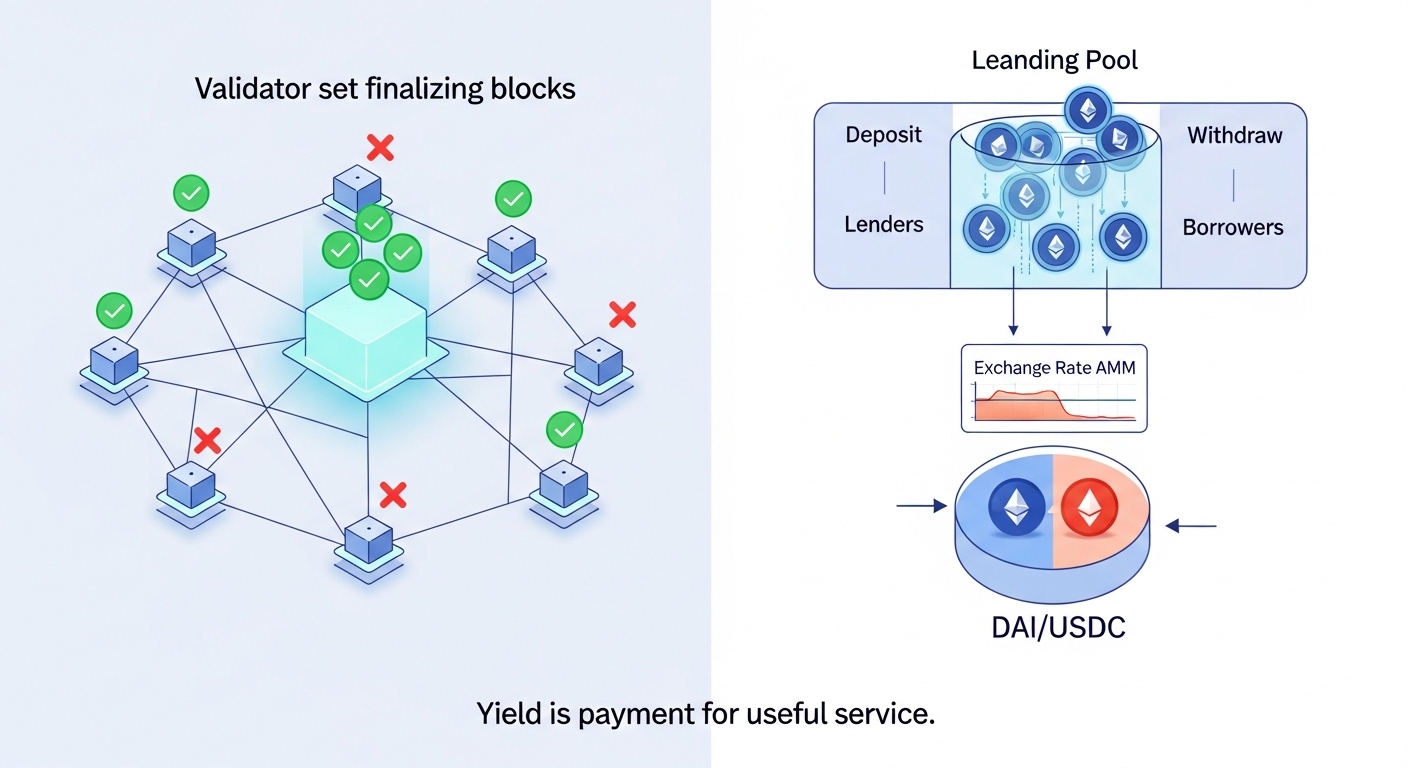
What staking really pays for
In proof of stake systems, validators commit capital and operate secure infrastructure. You earn rewards because your capital and your validator help the network finalize blocks and maintain liveness. Rewards are a function of:
- The network’s reward schedule and inflation policy
- Your stake share and validator performance
- Penalties for downtime or misbehavior, known as slashing
- Fees from transaction activity where applicable
The expected return is not free money. It compensates for operational risk, illiquidity during unbonding, and the possibility of penalties if the validator behaves incorrectly.
What conservative DeFi really pays for
In lending and liquidity protocols, conservative returns come from providing useful balance sheet services:
- Lending large cap assets or stablecoins to well collateralized borrowers
- Supplying liquidity to stable or blue chip pools where fee revenue is predictable
- Buying short duration instruments that are tokenized and settled on chain
The expected return compensates for smart contract risk, oracle risk, borrower concentration, and market volatility. The conservative approach accepts lower rates in exchange for lower probability of loss.
A Risk Taxonomy You Can Actually Use
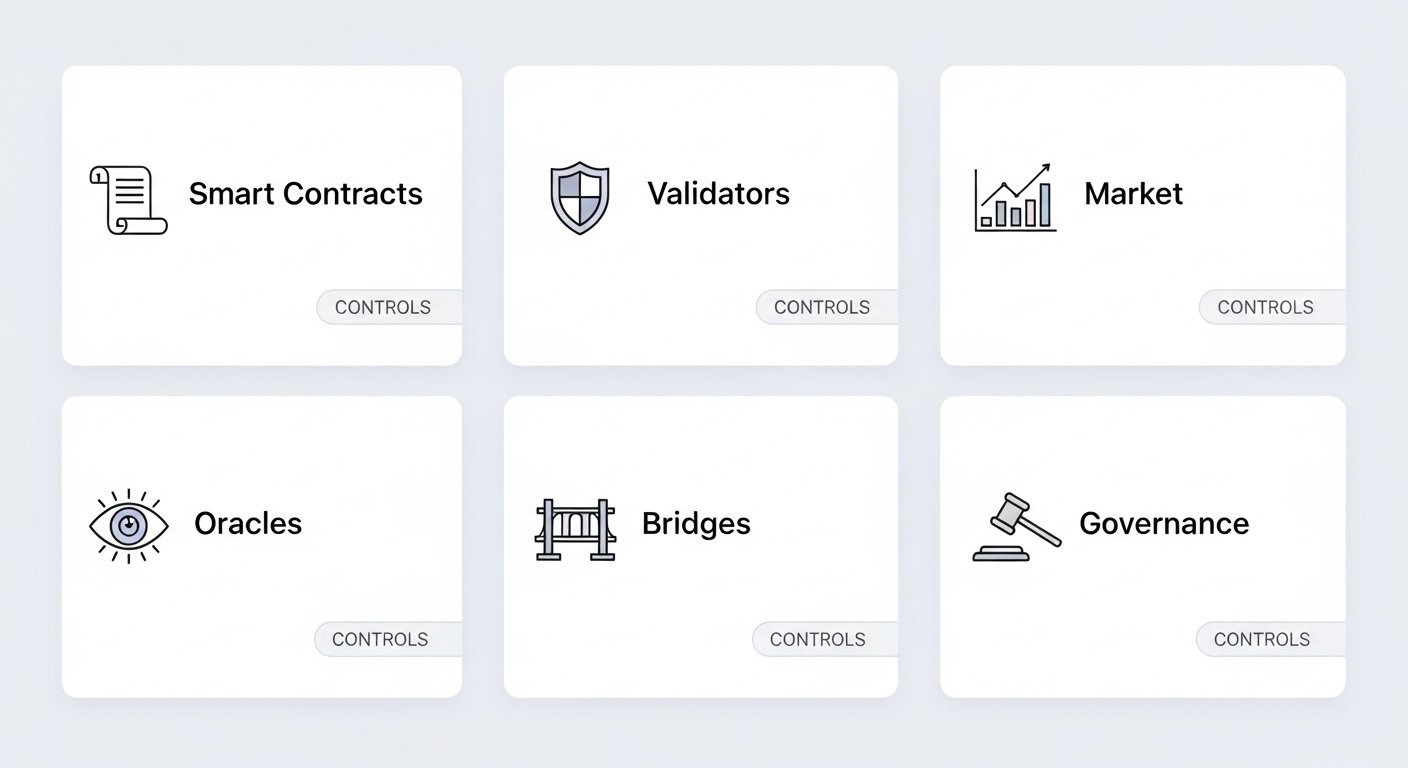
Treat risk as a checklist rather than a vague concern. Before staking or depositing, classify each position across the following dimensions.
Smart contract risk
- Code bugs, upgrade errors, and incorrect assumptions
- Access control that allows privileged actors to change parameters
- Incomplete test coverage or missing formal verification
Control: prefer battle tested code, multiple independent audits, slow upgrade timelocks, and public postmortems for past incidents.
Validator and operator risk
- Validator downtime that reduces rewards
- Double signing or key compromise that triggers slashing
- Single operator concentration that links many delegators to one point of failure
Control: choose validators with documented practices, diverse infrastructure, and visible performance records. Favor distributed sets rather than a single large operator.
Economic and market risk
- Liquidity drying up during stress
- Abrupt changes in incentive programs
- Borrower liquidations that impact pool health
Control: favor pools with deep, organic liquidity and conservative collateral rules. Monitor utilization and liquidation buffers.
Oracle and price feed risk
- Price manipulation in thin markets
- Oracle delays during volatile periods
- Overreliance on a single data source
Control: rely on protocols with robust oracle architecture, multiple data sources, and clear fallback rules.
Bridge and interoperability risk
- Cross chain claims that depend on third parties
- Wrapped assets with uncertain redemption
- Message relayers that can be censored
Control: minimize reliance on wrapped assets for principal positions. Prefer native assets and canonical bridges for essential transfers.
Governance and upgrade risk
- Rapid, unvetted upgrades that change risk assumptions
- Privileged roles that can pause or seize funds
- Voting power concentrated in a few wallets
Control: read the governance docs, confirm timelocks, and check whether emergency powers are narrowly scoped and transparent.
The Conservative Yield Pyramid
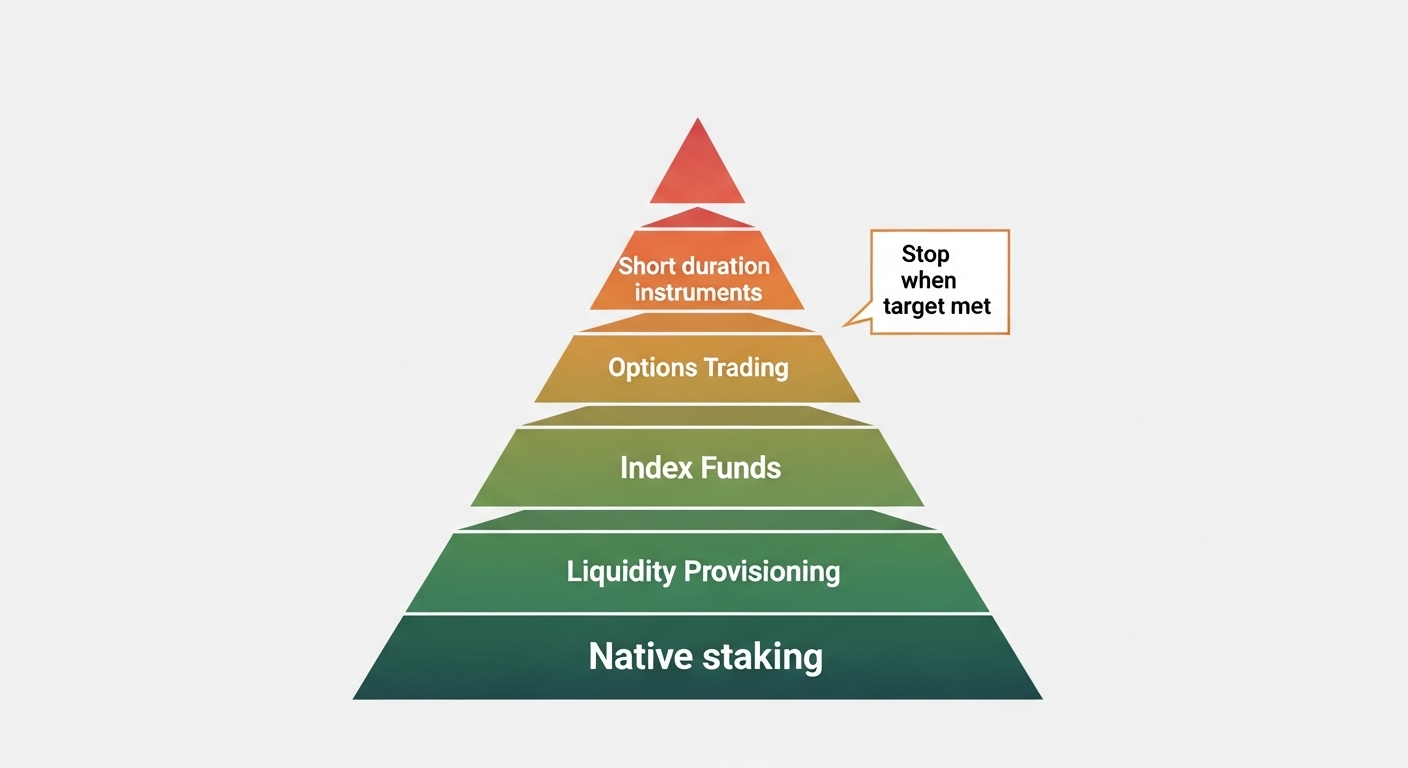
Think in layers, from safest to most experimental. Allocate top down until your yield target is met.
- Native staking of large caps: Baseline return with transparent rules. Illiquidity exists during unbonding, but the model is clear.
- Liquid staking on top of native staking: Convenience and composability, but adds a second contract layer. Size smaller than native.
- Conservative lending with overcollateralization: Blue chip collateral, proven liquidation engines, and mature oracles.
- Stablecoin liquidity in well balanced pools: Low volatility pairs where fees and volume are steady.
- Short duration, tokenized yield instruments: Conservative duration, clear redemption, and transparent holdings.
Stop when the portfolio level yield requirement is met. You do not earn extra credit for using more layers.
Position Sizing Rules That Prevent Regret
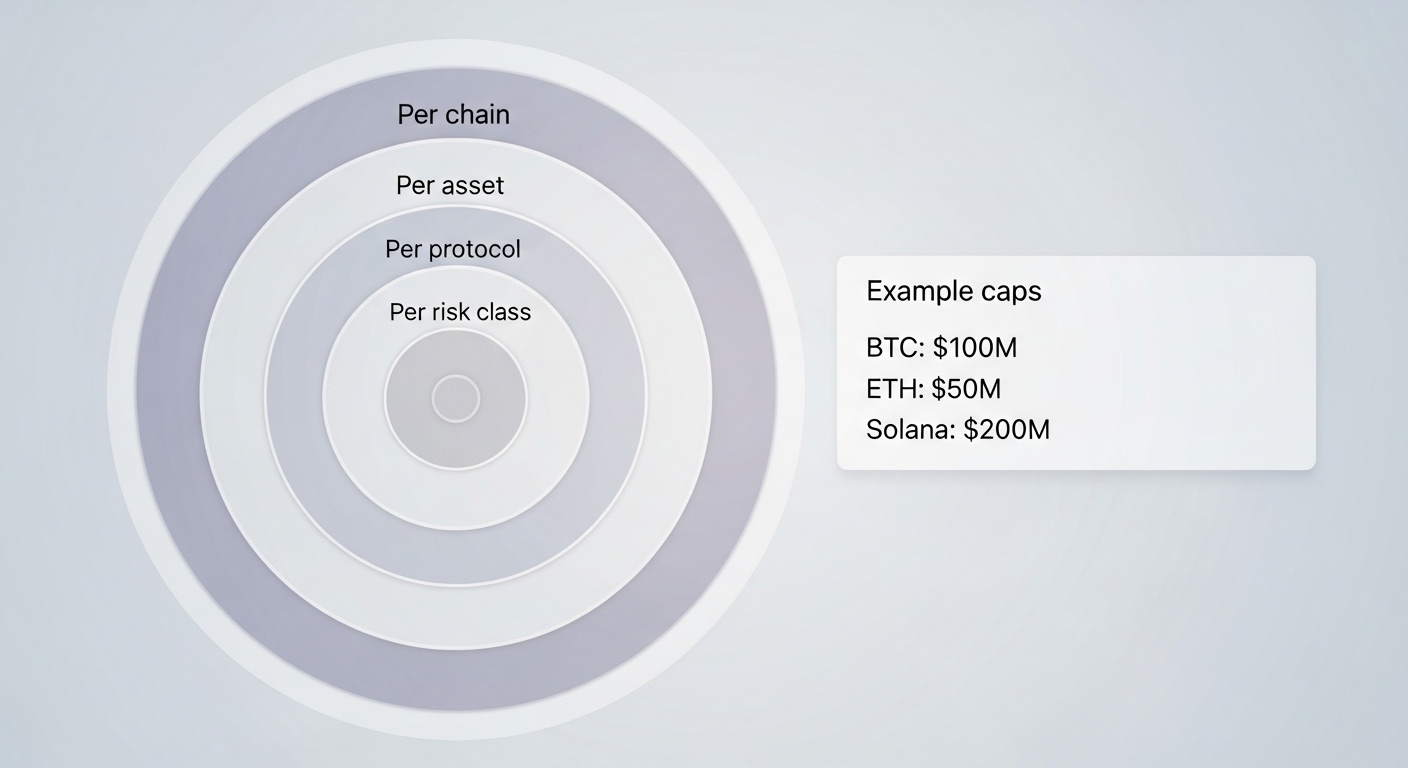
The four caps
- Per asset cap: no single token exceeds a preset share of the portfolio.
- Per protocol cap: no single protocol exceeds a preset share of the portfolio.
- Per risk class cap: for example, liquid staking derivatives capped at a smaller percentage than native staking.
- Per chain cap: avoid concentration on a single chain for operational resilience.
A practical starting point for a conservative or balanced investor:
- Native staking of a core asset: up to 25 percent of total portfolio
- Liquid staking derivative of the same asset: up to 10 percent
- Lending of large caps and stablecoins: up to 15 percent
- Stablecoin liquidity positions: up to 10 percent
- Short duration tokenized yield: up to 10 percent
Adjust downward if you are new to chain operations, and increase only after several months of stable monitoring.
Validator Selection, Without Guesswork

A clear validator checklist
- Uptime history across at least six months
- Documented infrastructure with geographic and provider diversity
- Public keys managed by hardware security modules or secure enclaves
- Commission rate that aligns incentives without encouraging corner cutting
- Published policies for double signing prevention and disaster recovery
- Transparent communication and a track record of incident reporting
Diversify your delegate set
Split delegations across multiple validators rather than concentrating with a single operator. This reduces correlated downtime and slashing risk.
Understand unbonding and exit windows
Native staking often requires an unbonding period before funds can be moved. Keep separate liquid reserves so you never have to interrupt the unbonding process to meet expenses or opportunities.
Liquid Staking Versus Native Staking
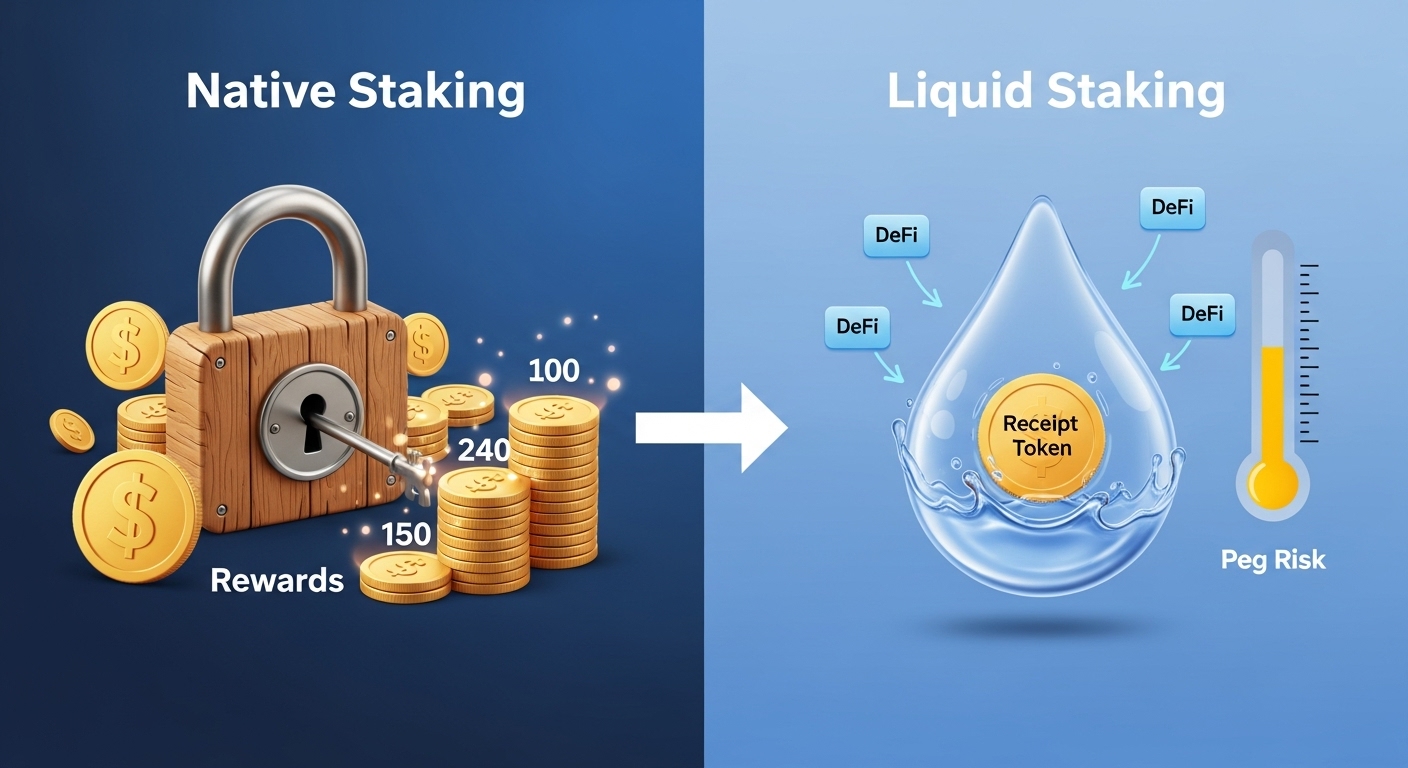
Benefits of liquid staking
- You receive a liquid token that represents the staked position
- You can trade, collateralize, or use the token in DeFi
- You avoid validator management overhead
Additional risks
- Extra contract layer and potential depeg in stress
- Liquidity reliance on secondary markets
- Exit queues if many users attempt to redeem at once
Sizing guidance: treat liquid staking as a convenience layer. Keep it smaller than your native stake and avoid using the same token as collateral across many protocols, which introduce stacking risk.
Restaking and Rehypothecation, With Caution

Restaking or reuse of staking receipts can increase yield. It also stacks risk. If the derivative token is used as collateral, a market shock can force liquidations and break peg dynamics. A conservative policy accepts lower headline yield to avoid reflexive scenarios. If you experiment, set a strict cap and disallow leverage on top of that cap.
Lending, The Conservative Way
What to lend
- Large cap assets with deep two sided markets
- Fiat pegged stablecoins with consistent redemption history
- Avoid long tail tokens as collateral or as lending assets
What to look for in a lending market
- Overcollateralization and conservative loan to value ratios
- Robust liquidation engine with clear penalty structure
- Multiple oracles with medianized feeds and circuit breakers
- Borrower concentration metrics and caps on single borrower exposure
- Public dashboards for utilization and liquidation health
Practical lending limits
- Keep utilization under review. High utilization indicates scarcity and potential rate spikes, but can also signal stress.
- Avoid depositing the same asset in multiple lending markets at size. Concentration across protocols increases correlated risk.
Liquidity Provision That Does Not Keep You Up At Night
Prefer low volatility pairs
Stablecoin pairs and closely correlated assets reduce impermanent loss. Fee revenue should cover variance in most market conditions. Accept that yield will be modest.
Pool design that matters
- Concentrated liquidity requires active management. If you cannot manage ranges, prefer passive pools.
- Dynamic fee tiers can help in volatile periods.
- External bribes and incentives may look attractive but often raise risk and complexity.
Exit and emergency procedures
Know how to withdraw liquidity quickly and test small withdrawals in calm conditions. Keep gas on the destination chain so you are never trapped without transaction funds.
Short Duration On Chain Yield
Short maturity instruments that exist on chain can be a useful cash management tool. Requirements for conservative use:
- Transparent holdings and daily price reporting
- Clear settlement rules and the ability to redeem within known timelines
- Compatibility with your wallets and operational tooling
- Jurisdictional eligibility for your entity
These instruments sit in the same sleeve as your stablecoin buffer and should be sized with liquidity needs in mind.
A Monitoring Runbook In One Page
Create a short document that lives next to your portfolio policy. The runbook contains the exact checks you perform on a schedule.
Daily checks
- Portfolio allocation against target weights
- Validator performance and pending alerts
- Utilization and health indicators for any lending positions
- Peg checks for any derivative or wrapped asset you hold
Weekly checks
- Review token approvals and revoke unused permissions
- Export a quick snapshot of balances and PnL
- Read incident channels for the protocols you use
Monthly checks
- Reconcile rewards and interest
- Test a small stake restake or redeem flow to ensure exits work
- Review governance proposals that affect parameters
- Rotate passwords and confirm that two factor authentication is active
Quarterly checks
- Full rebalance to targets
- Cold storage and seed backup verification
- Protocol audit review and changelog review
- Stress test. Assume a 30 percent market drop and confirm that you would not need forced sales
Document the exact dashboards and URLs you consult so anyone on the team can perform the checks.
How To Read an Audit Without Being a Security Engineer
- Scope first: Confirm what contracts and versions were audited. If the scope excludes key modules, risk remains.
- Severity and status: Note critical and high findings and whether they are resolved, mitigated, or acknowledged.
- Assumptions: Read the section that lists assumptions and trust boundaries. Many exploits live outside the audited scope.
- Follow up audits: Check for multiple independent firms and dates after major upgrades.
- Timelocks and upgradeability: An audit is not a blanket warranty. If contracts are upgradeable, require time delays and public announcements before changes take effect.
Incident Response Plan
When something breaks, speed and clarity matter. Keep a short, written plan.
- Freeze new deposits: Do not add capital until you understand the issue.
- Triage exposure: List every position that touches the affected protocol, asset, or chain.
- Reduce smart contract exposure first: Withdraw liquidity or repay loans where exits are still open.
- Avoid congested bridges: If cross chain movement is necessary, use canonical routes and expect delays.
- Record everything: Keep transaction hashes, timestamps, and a short timeline.
- Communicate internally: Share the plan with stakeholders and assign tasks.
- Review after the event: Update your runbook and limits based on lessons learned.
Practical Examples With Numbers
Example 1. Native staking allocation
- Total portfolio: 100,000 dollars
- Target native staking in a core asset: 20 percent
- Planned stake: 20,000 dollars across four validators, 5,000 each
- Monitoring: daily uptime feed, weekly check of commission and performance
- Exit plan: keep 5,000 dollars in liquid reserves to cover needs during unbonding
This example keeps validator exposure diversified and avoids operational pressure during exit windows.
Example 2. Liquid staking with conservative size
- Total portfolio: 100,000 dollars
- Liquid staking cap: 7 percent, or 7,000 dollars
- Use case: liquidity in DeFi for small, tested strategies
- Risk controls: automatic alerts for peg deviation, weekly review of secondary market depth
- Exit plan: if discount exceeds a defined threshold for more than 24 hours, reduce position by half
This recognizes convenience while containing derivative risk.
Example 3. Lending stablecoins with strict guardrails
- Total portfolio: 100,000 dollars
- Stablecoin lending cap: 8 percent, or 8,000 dollars
- Protocol screen: overcollateralized, audited, medianized oracles, visible liquidation engine
- Monitoring: utilization kept below a predefined level, borrower concentration monitored monthly
- Exit plan: full withdrawal test monthly with a small amount, full exit if utilization remains pinned at 100 percent for several hours
This favors capital preservation over headline yield.
Compliance, Accounting, and Documentation
- Jurisdiction check: Confirm that staking and DeFi activities are permitted for your entity.
- Record keeping: Store CSV exports and monthly snapshots in a versioned repository.
- Reward classification: Classify staking rewards and interest correctly for your local tax rules.
- Audit trail: Keep a simple table with position start date, size, rationale, risk class, and exit conditions.
A clean paper trail lowers stress during reviews and simplifies decision making.
Common Pitfalls And How To Avoid Them
- Chasing yield without understanding risk: If you cannot describe how the yield is generated in two sentences, do not fund it.
- Stacking leverage across layers: Using a derivative token as collateral across many protocols magnifies risk. Keep leverage out of conservative sleeves.
- Ignoring unbonding constraints: Liquidity mismatches create forced selling elsewhere. Keep cash reserves.
- Overusing a single chain: Outages can block exits when you most need them. Diversify operational paths.
- Skipping small test transactions: Always start small when interacting with a new contract, bridge, or chain.
A One Page Strategy You Can Paste Into Your Docs
Objective: Earn conservative yield while preserving principal.
Scope: Native staking, liquid staking, overcollateralized lending, low volatility liquidity pools, short duration on chain instruments.
Limits:
- Native staking of core asset: up to 25 percent of portfolio
- Liquid staking derivative: up to 10 percent
- Conservative lending: up to 15 percent
- Stable liquidity pools: up to 10 percent
- Short duration instruments: up to 10 percent
- Single protocol: up to 10 percent
- Single chain: up to 50 percent
Entry rules:
- Two independent audits, or battle tested code with public postmortems
- Transparent governance with timelocks for upgrades
- Clear oracle design and liquidation rules for lending
- Peg and redemption mechanics published for derivatives
Monitoring cadence:
- Daily allocation, validator status, utilization, and pegs
- Weekly approvals review, unknown transactions, and incident channels
- Monthly exit tests, performance snapshots, and governance review
- Quarterly rebalance and cold storage checks
Exit rules:
- Peg deviation beyond threshold for more than 24 hours
- Sustained 100 percent utilization without clear resolution plan
- Critical audit findings without timely mitigation
- Governance changes that remove timelocks or concentrate power
Paste this into your internal wiki, add the specific dashboards and addresses you use, and assign owners for each check.
Frequently Asked Questions
Is native staking always safer than liquid staking?
Native staking removes one contract layer and avoids reliance on secondary market liquidity, which simplifies risk. Liquid staking introduces convenience and composability, but it adds smart contract and peg risk. A conservative plan treats native staking as the base and keeps liquid staking as a smaller complement. If you need to use liquid staking tokens in DeFi, set strict caps and monitor peg health with alerts.
How much of my portfolio should earn yield at any time?
A balanced investor can place between 30 and 50 percent of the portfolio into yield positions, with most of that in native staking and conservative lending. The exact number depends on your liquidity needs, your rebalancing schedule, and your comfort with operational tooling. Always keep a cash sleeve in stablecoins and short duration instruments so you are never forced to unwind a productive position to meet a short term need.
What is a realistic target for conservative on chain yield?
Targets should be set by risk, not by a headline number. Native staking usually offers a baseline that reflects network conditions. Conservative lending and stable liquidity pools add a modest increment. If a quoted rate looks unusually high, ask what risk you are underwriting. Sustainable returns come from clear services provided to the network or to borrowers, not from opaque emissions.
How do I evaluate a lending protocol without reading every line of code?
Focus on structure and transparency. Confirm overcollateralization and conservative loan to value ratios. Review the oracle design and liquidation process. Check dashboards for borrower concentration and utilization. Read the audits and look for multiple firms and follow up work after major upgrades. Ensure governance has timelocks and that emergency powers are narrow and documented.
What is the single most important operational habit?
Always test with a small amount before committing size. This habit catches network congestion, fee misestimates, wrong addresses, and unfamiliar approval flows. It also builds muscle memory so that larger transactions are calm and predictable. Small tests are the cheapest form of risk management you will ever buy.
Can I use yield positions as collateral to increase returns?
You can, but it changes the risk class of the position. Collateralized yield introduces leverage and liquidation risk. A conservative policy keeps yield sleeves unlevered. If you experiment, limit size, avoid rehypothecation across many protocols, and write a clear stop rule that triggers de-risking before liquidations.
How often should I review and rebalance the yield sleeve?
Monthly is a practical cadence for most investors. Pair it with your wider portfolio review so that allocation, performance, and security are evaluated together. Rebalance more frequently only if a metric breaches its threshold, such as a peg discount, pinned utilization, or a governance change that alters risk assumptions.
What should I document for compliance and audits?
Keep a position register that lists start date, asset, protocol, chain, size, risk class, and exit conditions. Store transaction hashes for entries and exits. Keep monthly snapshots of balances and rewards, and save audit links. A simple, consistent paper trail makes internal and external reviews efficient.
Glossary
- Proof of Stake (PoS): Consensus where validators lock native tokens to secure the network and earn rewards.
- Validator: Operator that proposes or attests blocks in PoS and shares rewards with delegators.
- Delegation: Assigning stake to a validator while keeping ownership of tokens.
- Commission: Validator fee deducted from rewards before paying delegators.
- Slashing: Penalty that burns part of the stake for double signing or serious faults.
- Downtime Penalty: Reduced rewards when a validator is offline or misses duties.
- Unbonding Period: Time required to unlock staked tokens before they can move.
- Finality: Point where a block is considered irreversible under protocol rules.
- Native Staking: Staking the base asset directly in the protocol without derivatives.
- Liquid Staking: Receiving a liquid token that represents a staked position for use in DeFi.
- Peg / Depeg: Intended one to one relationship between a derivative and its base asset, and a lasting break of that relationship.
- Restaking: Reusing staked security to provide additional services, which stacks risk.
- Rehypothecation: Using a received asset as collateral again in another protocol.
- Overcollateralization: Borrowers must post collateral worth more than the loan.
- Loan to Value (LTV): Borrow size divided by collateral value, capped by the protocol.
- Health Factor: Indicator of how close a loan is to liquidation, values above one are safer.
- Liquidation Threshold: Collateral value at which a loan can be liquidated.
- Liquidation Penalty: Extra fee charged to a borrower when a position is liquidated.
- Utilization: Share of a lending pool currently borrowed; sustained highs can signal stress.
- Oracle: Service that publishes prices and data to smart contracts.
- Medianized Feed: Oracle method that aggregates multiple sources and uses the median to reduce outliers.
- TWAP: Time weighted average price used to damp short spikes.
- AMM: Automated market maker that quotes swap prices from pooled liquidity.
- Impermanent Loss: Value difference between providing AMM liquidity and holding assets separately.
- Concentrated Liquidity: Allocating AMM liquidity to chosen price ranges for higher efficiency.
- Stable Pair: Pool of assets that track similar values, such as two stablecoins.
- Dynamic Fee: AMM fee that changes with volatility or volume.
- Incentive Program: Extra token rewards used to direct liquidity or votes.
- Smart Contract Risk: Loss due to bugs, upgrade errors, or flawed assumptions.
- Upgradeable Proxy: Contract pattern that allows logic upgrades and needs governance safeguards.
- Timelock: Delay between proposing and executing privileged actions.
- Pause Guardian: Role that can halt a protocol during incidents within a defined scope.
- Governance: Process for changing parameters or logic, often token based with timelocks.
- Bug Bounty: Program that pays researchers for responsible vulnerability disclosure.
- TVL: Total value locked in a protocol, a rough usage proxy.
- Risk Reserve: Funds set aside to absorb losses or bad debt.
Conclusion
Conservative yield in crypto is a craft. You earn steady returns by providing useful services, you set limits that contain risk, and you write a short policy that guides action when markets are loud. Start with native staking, add measured liquid staking if you need composability, lend only to well designed markets with transparent rules, and keep a cash sleeve that covers your liquidity needs. Monitor with a one page runbook. Document every change. Review monthly and rebalance quarterly.
The result is not a flashy number. The result is a portfolio that grows through many market conditions, that avoids avoidable losses, and that gives you confidence to stay invested through the cycle.
About Bitunix
Bitunix is a global cryptocurrency derivatives exchange trusted by over 3 million users across more than 100 countries. At Bitunix, we are committed to providing a transparent, compliant, and secure trading environment for every user. Our platform features a fast registration process and a user-friendly verification system supported by mandatory KYC to ensure safety and compliance. With global standards of protection through Proof of Reserves (POR) and the Bitunix Care Fund, we prioritize user trust and fund security. The K-Line Ultra chart system delivers a seamless trading experience for both beginners and advanced traders, while leverage of up to 125x and deep liquidity make Bitunix one of the most dynamic platforms in the market.
Bitunix Global Accounts
X | Telegram Announcements | Telegram Global | CoinMarketCap | Instagram | Facebook | LinkedIn | Reddit | Medium
Disclaimer: Trading digital assets involves risk and may result in the loss of capital. Always do your own research. Terms, conditions, and regional restrictions may apply.









