
Despite all the innovation in blockchain technology, it still feels like different blockchains live in separate worlds. One chain may host powerful DeFi protocols, another might offer cheaper fees, while others provide unique liquidity pools or digital assets. But here’s the challenge: how do you seamlessly transfer value, swap tokens, or communicate across these multiple blockchains without being locked into one chain? This is where cross-chain bridges come in – a critical innovation in the crypto industry that allows users to move assets across multiple networks.
Yet, as with every revolutionary step, bridges come with both security risks and opportunities. In fact, cross-chain bridges are among the most vulnerable points in blockchain ecosystems, often targeted in some of the largest hacks in DeFi history. So, should users and developers trust these systems, or are they ticking time bombs in the decentralized future? Let’s dive deeper.
[ez-toc]
Why Cross-Chain Bridges Exist

Blockchains, by design, are closed systems. The Bitcoin network doesn’t natively talk to Ethereum, and the Solana network doesn’t directly interact with Polygon. Each chain uses its own protocols, consensus mechanisms, and native tokens. This fragmentation makes the broader DeFi ecosystem less efficient and prevents full interoperability.
Cross-chain bridges were developed to solve this problem. They act like translators between different networks, allowing users to transfer crypto assets from one blockchain to another. For example, a user can lock ETH on Ethereum (the source chain) and receive wrapped ETH (a wrapped asset) on Avalanche (the destination chain). This enables access to protocols, liquidity, and rewards across multiple blockchains.
Without bridges, the idea of multi-chain DeFi would be impossible. Bridges unlock new opportunities for providing liquidity, accessing decentralized applications on other networks, and diversifying strategies across chains.
How Cross-Chain Bridges Work
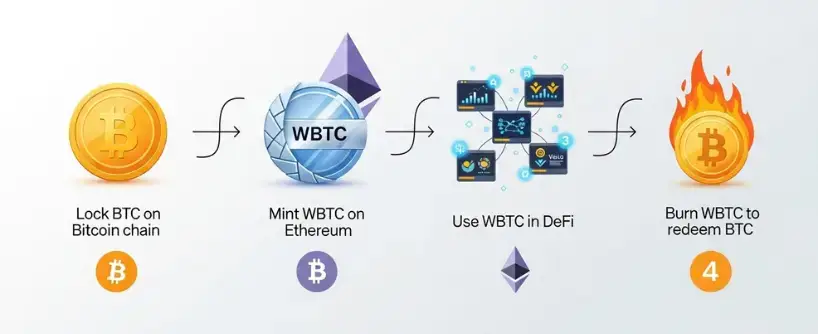
Most bridges rely on smart contracts that lock tokens on the source chain and issue wrapped versions on the destination chain. Once the user decides to move their assets back, the wrapped tokens are burned, and the original tokens are released.
Here’s a step-by-step example:
- You Lock Your Assets: Let’s say you want to use your Bitcoin (on the Bitcoin blockchain) in a multi-chain DeFi application on Ethereum. In models like Wrapped Bitcoin (WBTC), you send your BTC to an authorized merchant, with custody managed by BitGo. Once confirmed, the custodian mints an equivalent amount of ERC-20 WBTC on Ethereum. To redeem, WBTC is burned, and the custodian releases your BTC back on the Bitcoin blockchain.
- The Bridge Mints a Representative Token: Once the bridge confirms it has your BTC, its corresponding smart contracts on the Ethereum network mint an equivalent number of wrapped BTC (WBTC) tokens. This WBTC is an ERC-20 token that represents your Bitcoin on the Ethereum blockchain.
- You Use the Wrapped Asset: You now have WBTC in your Ethereum wallet. You can use this to swap tokens, provide liquidity in liquidity pools, earn rewards, and interact with any DeFi protocols that support it.
- You Burn to Redeem: When you want your native Bitcoin back, you send your WBTC back to the bridge’s Ethereum smart contract to be “burned” (destroyed). Upon verifying this, the bridge releases your original BTC from custody on the Bitcoin blockchain back to your wallet.
This entire process is powered by complex smart contracts and often relies on external validators or oracles to confirm transactions, which is where things can get tricky.
The Other Side of the Coin: Understanding Cross-Chain Bridge Security Risks

While bridges are fundamental to the vision of a connected DeFi ecosystem, they have become the single biggest security vulnerability in crypto. According to Chainalysis, approximately 69% of all cryptocurrency stolen in 2022 originated from bridge hacks, underscoring the vulnerability of these systems at the time.
Why are cross-chain bridges so vulnerable? The answer lies in their complexity. A bridge isn’t just one smart contract; it’s a system of contracts across multiple chains that must communicate and coordinate perfectly. This expanded “attack surface” gives hackers more points to exploit. Let’s break down the most common security risks:
Smart Contract Vulnerabilities
Bugs in the code of the smart contracts that power the bridge are a prime target. A tiny flaw in the logic can allow an attacker to drain funds from the bridge’s liquidity pools. Unlike a hack on a single dApp, a bridge hack compromises the entire treasury of cross-chain assets held in custody.
Centralization and Trust in Validators
Many bridges rely on a “federation” or a set of external validators to confirm transactions between chains. If this group is too small or requires too much trust (a “trusted” rather than “trustless” model), it becomes a target. If an attacker compromises a majority of these validators’ private keys, they can approve fraudulent transactions and steal all the funds. This was the cause of several major bridge hacks.
The Perils of Minted Assets
The system of wrapped assets introduces economic risk. What happens if the bridge holding the locked native tokens gets hacked? The wrapped assets on the other chain suddenly become unbacked, essentially turning into worthless digital certificates. Their value would plummet to zero, devastating everyone who held them.
Transaction Malleability and Consensus Attacks
Some bridges have failed due to verification flaws, such as bugs in message or signature validation. For example, in 2022, the Wormhole bridge exploit bypassed signature verification, allowing attackers to mint unbacked assets.
The message is clear: the very thing that makes bridges powerful, their ability to connect different protocols, also makes them inherently critical security challenges.
Real-World Examples of Bridge Vulnerabilities
- Poly Network Hack (2021): Attackers exploited a flaw in the smart contract, draining over $600 million.
- Wormhole Hack (2022): Over $320 million was stolen when attackers bypassed verification of wrapped assets.
- Ronin Bridge Hack (2022): North Korean-linked hackers compromised validator nodes, stealing over $600 million.
These examples highlight how cross-chain activity can expose users to extreme risks if security measures are not properly implemented.
The Path to Secure Cross-Chain Interoperability

The frequency and scale of bridge hacks have sent a shockwave through the industry, forcing developers and organizations to double down on security. The goal is no longer just to build bridges, but to build fortified ones. Here are the key security measures being implemented:
Advanced Cryptographic Proofs
The emerging solution is moving towards bridges that use cryptographic proofs (like zero-knowledge proofs) to verify state transitions between chains without relying on third-party validators. This creates a more trustless and secure system.
Robust Audits and Bug Bounties
Before launch, the bridge code is undergoing more rigorous, multi-round audits from top security firms. Continuous bug bounty programs also incentivize white-hat hackers to find vulnerabilities before malicious actors do.
Decentralized Validation Networks
Instead of a small set of validators, newer interoperability protocols are using large, decentralized networks of nodes (similar to those that secure major blockchains like Ethereum) to verify cross-chain transactions. It’s much harder to compromise a large, randomly selected set of nodes.
Risk Mitigation and Insurance
Some protocols are experimenting with insurance funds built into their design to cover users in the event of a catastrophic failure, adding an extra layer of protection for users’ funds.
The Unmissable Opportunity: Why We Build Bridges Despite the Risks

After that sobering list of risks, you might wonder: why do we even bother? The answer is that the opportunities and benefits that cross-chain bridges unlock are so transformative that the industry must solve the security puzzle.
Cross-chain bridges are the foundational pillars for the next era of the internet: the multi-chain world.
Unlocking True Interoperability
They break down the walls between isolated networks, allowing different networks to share value, data, and functionality. This is critical for the long-term growth of the entire crypto space.
Supercharging Multi-Chain DeFi
Bridges are the engine of multi-chain DeFi. They allow liquidity to flow freely to where it’s needed most, making liquidity pools deeper and more efficient across all chains. This leads to better yields for lenders and better rates for borrowers.
Expanding User Choice and Access
Bridges empower users. You are no longer limited to the applications on one chain. You can chase the best yields on Ethereum, enjoy low-cost gaming on a sidechain, and hold your favorite native tokens on Solana, all with the same portfolio of assets.
Fostering Innovation for Developers
Developers can build decentralized applications (dApps) that utilize the unique strengths of multiple networks. For instance, an app could use Ethereum for its robust security and finality while offloading heavy computation to a more scalable chain, all seamlessly connected by a cross-chain protocol.
The promise is an internet of value that is borderless, efficient, and open to all. That is a future worth building and securing.
The Future of Cross-Chain Interoperability
The cryptocurrency industry is pushing hard toward secure, scalable, and interoperable protocols. Innovations like Chainlink’s Cross-Chain Interoperability Protocol (CCIP) and platforms like Symbiosis aim to provide more secure ways of connecting multiple chains.
We are also seeing research into trust-minimized bridges that don’t rely heavily on centralized validators. Instead, they use cryptographic proofs to verify transactions across chains, reducing reliance on human trust.
In the coming years, we can expect cross-chain interoperability to become a foundation of blockchain adoption. From digital assets to data and beyond, bridges could evolve into the core infrastructure enabling communication across various protocols and blockchain ecosystems.
Conclusion
Cross-chain bridges represent both the most promising opportunity and the most critical challenge in blockchain technology today. The question for users, developers, and organizations is simple: Can we make these systems secure enough to trust with billions in value? The answer will determine how fast blockchain achieves its vision of a truly connected and decentralized financial future.
As a user, the key is to be informed. When interacting with any bridge:
- Prefer bridges that have undergone multiple audits and have a proven track record.
- Know whether the bridge uses a more decentralized or centralized security model.
- Never bridge more than you are willing to lose.
The work being done by organizations and developers to implement stronger security measures is accelerating. The bridges of tomorrow will be far more robust and secure than those of yesterday.
The chasm between chains is being crossed. The bridges are being built. And with careful construction, vigilance, and innovation, we will create a connected digital world that is both powerful and secure. The multi-chain future depends on it.
FAQs
What are cross-chain bridges and why are they important?
They let users move digital assets across different blockchains, enabling multi-chain DeFi and cross-chain interoperability.
Are cross-chain bridges safe to use?
Bridges can be vulnerable to hacks and bugs. Using audited contracts and decentralized validators improves security.
What opportunities do cross-chain bridges offer?
Users can swap tokens, access liquidity pools, earn rewards, and explore multi-chain DeFi strategies.
Disclaimer: Trading digital assets involves risk and may result in the loss of capital. Always do your own research. Terms, conditions, and regional restrictions may apply.

